tv U.S. Senate CSPAN January 8, 2013 9:00am-12:00pm EST
9:00 am
from a country in which we know there's a high degree of terrorist activity and al qaeda activity? >> its -- the screening level is calibrated some extent by the country of origin, but we also we settle refugees from afghanistan. we we settle refugees from parts of africa where there's also turmoil. though in fact what's incumbent upon all of us to do at the interagency and with intelligence community is to look at the specific, as you said, the specific intelligence that comes from rising in those situations. i would defer to my colleague -- >> let me just pursue this. i'm going to ask you to go into those questions but you were telling sort of a generalized approach to the humanitarian immigration, and i can see somebody from camby or some other, ethiopia where we don't know, could be questionable but we don't have the same degree of current, you know, the issues, but with those in iraq, afghanistan, jordan, syria,
9:01 am
egypt, do we have some kind of a method in which there is a specific heightened level of scrutiny for those who are seeking to come into this country? my opening question, i know, related to asking for your response with regard to the 58,000 iraqi refugees who are already here. so i'm sort of giving you two questions, but i want you to answer about these other countries now, and then get back to when asked about the 58,000 iraqi refugees. >> let me do my best, but i think i'm again going to have to defer for specificity for my department of homeland security college. the types of checks that are implemented for refugees are largely similar, i think the difference, but again my colleagues will expand pond scum is a type of information that is available to us from those very checks. so when my colleagues talk about using databases, fingerprint
9:02 am
databases from iraq, those definitely are just used for iraqi refugees. i think that is the discriminating factor, the types of intelligence holdings that we have in our ability to check against those holdings. i think on the second question about what is being done for the people who have already arrived, again i would defer to my dhs colleagues have been much more involved in that issue. >> ms. strack and ms. scalici, either of you who wants to add to this, i guess the implication on that is somehow there is a level of basic intelligence that exists which is higher in those countries that we have concerns about nefarious activity than in others, is that accurate? and how is that -- be responsive to my question. >> thank you, mr. chairman. i'd like to start with this briefly, operational response, and then invite my colleague to speak more in depth on the intelligence front. i would say operationally, what
9:03 am
you're suggesting that the program ought to have heightened scrutiny on iraqis is, in fact, what happened. this was a chronology, and when the united states government announced large-scale resettlement of iraqis in 2007, we immediately looked at what should we be doing in light of this particular population, which was different, the nation out of we've not been reselling a great deal. we look at what enhancement we could bring on board that would address this new population. and that's when we create the partnership with dod. initially that was iraqi focused. later when we work with the national -- >> was this in 2007? >> 2007. later when we identified additional capacity a new partnership, that initially was focus on iraq at because but we learn by doing that was learned that heightened level of checks which was initially oriented towards iraqi applicants, we
9:04 am
expand to applicants of all nationality. so really we use the iraqi program to raise the bar across the board for other nationalities. >> there was some 20, 25,000 a year for a features are coming out of iraq. is that about right? >> i believe the high point is 18,000. >> i mean, that still 18,000 a year. did you have the resources and capacity to do some kind of fairly narrow assessment of those 18,000 for their able to be granted? >> yes, sir we did. that's where i would like to defer to my colleague to explain in further detail. >> thank you. i think it's fair to say that in 2007 with a large scale processing of iraqis begin, certainly the security and better programs ahead in place at the time was strong but they were not -- we learned a lot since then. we work with and agency partners to strengthen security and betting programs we have in
9:05 am
place. as ms. strack indicated there's a chance that procedures were initially applied to iraqi refugee applicants come expanded overtime to other high-risk populations to now as with all acknowledged to include all refugee applicants regardless of the country of origin within the age ranges of 14-65. so we believe that the greatly enhanced security and betting which allows us to draw upon all intelligence, intelligence and other data on applicants is greatly enhanced our ability to identify derogatory information on applicants for the refugee program. at the same time, we recognize the fact that a number of iraqi refugees into the country before the enhanced security vetting procedures were put into place by the interagency. so what we have done as an interagency process is to go back into retroactive checks on those individuals that were
9:06 am
earlier admitted to the united states them and any relevant information that comes to light is then shared with relevant target community or law enforcement agencies as appropriate. one other thing i think you would mention as well, not only to have analyst or look at all the relevant intelligence and data at the time that an applicant originally puts forward their applications, we review it again before the applicant actually enters the united states in case any derogatory information has arisen in the intervening time. so we do believe again the interagency process of drawing on more intelligence and data than we ever did before, as well as the returning and the retroactive check is greatly enhance our ability to identify individuals of concern. >> ms. scalici, thank you. my time has expired. i will follow up with some questions, but now i recognize the ranking member for whatever
9:07 am
questions that she may have, ms. hahn. >> thank you. i think for me i would just, we'll simply and my opening testimony i talked about the arrests of the iraqi refugees and how there was information available earlier that might have led us to believe that they could cause some trouble in our country. how did we miss that initial information? and could you speak to what are we doing, i hear vague comment about information sharing but we know that these key, as we move forward. that was one of the one lessons we learned from 9/11. so what, without divulging any classified information, how did we miss that information the first time around? and what can you tell us that will give us some confidence
9:08 am
that we really are able to look at all the data available out there to make responsible decisions as we move forward in this refugee program. >> well, for those two individuals of concern that we've been talking about, at the time they made their original application to enter the refugee program in the united states, both they are biographic and the biometric information that we have available to them, on them at the time and it was used for the screening process came in clean. so we did not have any derogatory information on those two individuals that we used as part of the screening effort when they entered the united states. in fact, the fingerprint clearance came through as well. from dod, fbi, as was dhs.
9:09 am
>> even though the fingerprints were found to been on a roadside bomb? >> that we have learned in the aftermath. i would have to defer to dod and the fbi for any specific information on that. but again, all the biographic as well as the biometric checks that were performed at the time did come back clean. but since that time as you have noted we've actually enhanced the program and the security checks, and we now draw upon a greater wealth of intelligence and data holdings on individuals seeking application to the refugee program which greatly enhances our ability to identify derogatory is, compared to earlier. >> does anyone else want to comment on that? so other than the recent iraqi refugee case, have there been many open-source cases of foreigners admitted through the refugee our immigration programs who have been associated with terrorism? and is there any evidence that terrorist groups are successfully exploiting this new
9:10 am
u.s. refugees commission broke or or any other refugee program for the specific purpose of gaining entry into the u.s. in committing an act of terrorism? >> in that regard, certainly we are concerned about potential for terrorist groups to exploit the refugee program. we certainly saw that in the case of the two individuals arrested in kentucky. although a point of clarification in that case. we don't actually believe that those two individuals deliberately sought into the united states through the refugee program with a specific intent on carrying out an attack here. but certainly the aftermath of the entry into the united states, given the continuing desire to support terrorist groups, in particular aqi, as was obviously the previous terrorist involvement had come to light. they were security risks. when we looked at the potential,
9:11 am
in the future for terrorist groups to exploit the refugee program, we do have concerns, hence we have enhanced security and vetting procedures that we have in place. and i will tell you that we have intelligence driven processes, regardless of the immigration program that a terrorist actors, just how to united states. we are reviewing intelligence on a regular basis, sharing that with in the agency partners and developing procedures by which would help to identify and for the screen individuals of concern. again, regardless of the way in which they plan to enter the united states. >> if i may follow-up, with respect to your question or information sharing. i did want to note that we in many ways that uscis we are customers of the agencies that hold security and national intelligence information, and it is a tremendously cooperative
9:12 am
relationship. we have relationship. the information flows, and it not only comes to us in order to help us make better decisions in individual refugee cases, there are instances where we are also able to share information back. so for example, if there is a latent fingerprint that has been identified from an ied or some other terrorist related purpose, if that applicant, if that individual appears as an applicant in the refugee program, we are able to associate biographic information with that person, a photograph with a person, a location with that person. and so we're able to enrich the watch list information in that regard. also, my colleagues at end of the division of uscis, our fraud detection and national security you know, have quite an elaborate program with liaison, with other agencies. so they have officers embedded
9:13 am
at the national counterterrorism center, terrorist screening center, interpol, with the joint with the joint terrorism task force is that both the national level, state and local. so that's a very important program for us to make sure that those agencies have the benefit of the immigration expertise embedded in their you know, and there are also eyes and ears for uscis to make sure we're getting information from those kinds of organizations that are important to us, not just for the refugee program but across the whole range of immigration benefits that we are responsible for. >> are you working with our fusion centers the? yes, ma'am. >> because i really think, i know we have conflicting reports sometimes on the success of those, but i know the ones where i come from in los angeles have been very valuable in helping to provide extremely important information that i believe has been forwarded some potential attacks in the country. >> we agreed spent i know i am over time but since it is just
9:14 am
you and me, i just have, i was just thinking, i am a strong supporter of quick immediate and responsible drawdown of our forces in afghanistan. i'm one of those that really would like to see -- speed up that timeline. but part of the responsible drawdown and includes providing opportunities for the afghan people. are we prepared, what's your projection as we wind that war down to a number of afghan refugees that may be seeking to come to this country? and let us do how your resources are and if you feel like that is going to be a major surge, or -- because the afghan refugees have been smaller in comparison to the iraqi refugees. i wanted to hear your projection as we go forward how you think that will all play out. >> thank you.
9:15 am
interesting question. so, on the afghan front, the program that we have that is parallel to the iraq program is a special visa program. i was legislated by congress, for those people have worked closely with our forces under embassy and other u.s. contractors. so that program is still ongoi ongoing. it's frankly been a bit slow getting off the market, frankly is now working over the last year, had i think 235 visas were issued, a total over the time of the program, 2117. so still fairly small but it continues. on the refugee side, the refugee situation in afghanistan is quite a bit different than the iraqi refugee situation. most afghan refugees for over 20 years have found shelter and protection in either pakistan or iran, and on the case, in the case of pakistan we have
9:16 am
supported the international efforts to help those refugees that are finding asylum in pakistan. most of those refugees are not seeking resettlement. they have looked over the last few years to see if there are pockets of refugees, especially, both in pakistan and iran that are in need of resettlement. we started to resettle some refugees from both countries. we have a very small program out of iran. we are obviously not operating inside iran but are taking those people to either romania or slovakia where we can process vulnerable women and families. so we don't, i think, projected large increase in the reseller program for afghanistan, but we continue to help and i think the neighboring countries that are providing asylum. where individuals might need protection as opposed to large waves of refugees. >> thank you.
9:17 am
>> mr. bartlett, you identified that you have a two-step process. first come you want to identify those who are eligible for this consideration, and then assure that they don't present a risk. explain to me how you identify when and how somebody is eligible for this process in the first place. >> sure. and that's more than a one step process, frankly, to identify people for resettlement. frankly, our largest partner is u.n. high commissioner for refugees, and they work throughout the world spent is that an american run organization or is this an international organization? >> it is an international organization. they operate in countries of refugee outflows as well as country for brevity's are received spent am i correct to say we have an international arbitration that is determining who should be emigrating to the united states of american? >> it would not be exactly
9:18 am
correct. what, what we did is we worked closely with unhcr in this regard to look at populations that are need of in resettlement. they are located in camps. they are basically at the ground level. there are hundreds and hundreds of thousands of refugees around the world who don't have a hope to go home anytime soon. >> how to distinguish, because it interesting and i notice you identified, that afghans would have a place of refuge in pakistan. we are now looking at jordanians, syrians. not as likely egyptians at this point although nobody is going to know what's going to happen there. how do you determine who may be able to find refuse within the region as opposed to the aung san suu kyi the only source of refuge spent this is certainly a diplomatic and diplomatic effort. so what -- hundred will provide asylum for refugees as they see
9:19 am
fit. that all countries are able to provide long-term support. and so that's something that we will engage bilaterally with, in terms of government, but we will also work multilaterally through the u.n. and other partners to see, so for example, syria, you bring up certain refugees. syrian refugees right now have moved into principally turkey and lebanon but moving also into jordan. those countries are hosting those refugees and we're supporting that effort. in the refugee, 99% of the refugees in this world would like to go home. as great a place as the united states or canada are for resettlement. the first preference is to go home to their families and their own country. so what we tried it is to support the effort to help people. right now again in turkey and lebanon and jordan, to remain in those places come to have protection, have services so that as the situation changes,
9:20 am
and hopefully the violence subsides, they can return home. so we are not looking at result in large numbers of syrian refugees at this moment. but again we are looking out to see if there individuals who, for example, may have protection concerns in turkey or lebanon and cannot stay there safely. so it's really a kind of a two-step process. in an emergency situation is really about providing assistance. and we provide about $200 million worth of assistance to syrian refugees, and allowing them an opportunity to go home as the situation changes. if the situation becomes protracted as it did with iraq iraqis, countries are sometimes unable to host you for an experienced -- anthony pigott time. after five, six years they would begin to look at who within the population might be in need of resettlement. >> i interrupted you with regard to how the criteria and eligibility, so is their
9:21 am
criteria that you look at in making those determinations as to who is eligible? >> there are. our program prides itself on the fact that we look largely out of vulnerabilities. we look at really protecting people who are vulnerable in a country that is violent. you know, our program provides a fairly broad range of services once people arrive. so we are working with them to help anchor them in the u.s. and help them gain self-sufficiency. but in terms of looking at criteria, again, we look at the vulnerability. their inability to stay in the situation of temporary asylum, and, frankly, their inability to go home. so as a situation becomes protracted, somalia is a good example, we know that there will be in the democratic republic of congo, these are two populations that won't have an opportunity to go home soon. so then we will look at just we
9:22 am
populations within a large community to see was the most vulnerable. often, women at risk without a husband, a has been is missing but with children, have protection concerns in a can't environment or in an urban environment. and so we will look at that population and want to identify those, those people. sometimes people with medical conditions, they can't be treated in a camp. and makes them again more vulnerable and we will look at those populations. so it's kind of a broad array of vulnerabilities that we try to assess. >> ms. strack and, therefore, could you identify, we're talking about those who are eligible for consideration. there has been an identification of an emphasis on those who have participated in assisting the united states efforts either in the military intelligence,
9:23 am
otherwise, nongovernment organizations have been put themselves into some peril. what is the distinction between those who are humanitarian versus those who have performed to the benefit of our interests and are therefore being given consideration because of the exposure that may result from that service? >> i would say the programs working in several ways to address both humanitarian concerns and those who worked side-by-side, employed directly by the u.s. or with you is affiliated organizations, ngos or media organizations. the siv program that was talked about is often conflated with reggie program but it's actually distinct. >> could you explain that to me, what siv stands for. i want to see how that is different from the other program. >> yes, sir. it stands for special immigrant visa program, and unlike the
9:24 am
refugee program, the fundamental focus of the refugee program is on whether someone has been persecuted, had been persecuted in the past or have could have a well-founded -- in the future come up based on a protected category, rape, religion, nationality, political opinion or membership in a particular social group. the siv program traditionally, special immigrant visa, usually based on service with the united states. this is something mr. bartlett is a little bit more of an expert on, but congress legislated a program, special immigrant visas, to say that those who have worked for the united states government, there are three subcategories within a special immigrant visa program. initially it was small, a translator with the military but it expanded beyond that to include industry employs. and really for them it's the fact of the service with the united states that makes them eligible. and when they come to the united states, both our agencies --
9:25 am
they don't come with the refugee. they come as a lawful permanent resident xo when they arrived they get a green card. based on their service. now, there are some individuals who may be eligible to apply for both programs. and have worked with the us embassy or the u.s. military so they're eligible to apply for a siv but they may very well be able to articulate a refugee claim because of that service they have also faced persecution. so we work, we work on the refugee side of the program, but individuals may choose which of those two avenues is better for them, which they think they can, operate more quickly, depend on whethewhether in iraq or somewhe else. >> do they operate on a parallel track, or is there some preference given to somebody who has served as an interpreter for our troops that are coming in,
9:26 am
out in the midst of the mountains in afghanistan? do they get a preference, or is there not any difference? >> i can tell you that they do operate on a parallel track. so an individual has the opportunity, an individual who is eligible has a opportunity to file for an siv, and begin that would be filed with the state department. and in the refugee program, having worked with the united states or a use affiliated organization is one of the criteria that can help you get access to the program, but it's not the sole criteria. >> the other thing i would like to follow up is, this has been such a good hearing and such a serious issue, but an important one. and again, we want to make sure that we continue this program, these programs, ensuring the safety of the refugees and the safety of the americans.
9:27 am
have you been briefed on any possible effect that sequestration might have on the departments and these programs? >> i think that i know it the state department with certain look at overall sequestration affects. i know also that our program, our program has been adequately funded in the past. and so i guess our expectation is that in the coming year that the program should be able to continue at a similar level. i think would be hard to say it would be the same level. but again, a lot of the infrastructure we have in place overseas as well as domestically, i think will remain. so i think the question will be probably what happens in the longer-term. i'm not able to answer that at
9:28 am
this point. >> uscis is in an unusual position in that most of our programs, including the refugee program, are funded through fees. so the feeds that are paid by applicants for other immigration benefits is what supports the refugee resettlement program for uscis. that being said my understanding is that the interpretation of sequestration is that it's most like will not affect just appropriate funds at our feet fun as well. that's a topic it is you, our budget office at uscis is in discussion with dhs headquarters on how to sequestration will affect uscis. >> thank you. we know our republican colleagues are going to do the right thing and make sure that we don't go over the cliff. i have complete confidence. spent as july.
9:29 am
-- >> as july. i appreciate as well, there's so many aspects to this hearing, and i do want to follow up on a couple of ones. i open by identifying this looking to the past, while at the same time we appreciate the continuing instability throughout the region as we go to the future. and both create challenges to our immigration process, those who have already gained entrance to the united states, those who we may be looking at in the future. i identified testimony from robert mueller which was public reported, and effective as accurate. it was before the house intelligence committees, and individuals who may have resettled here in the united states that have some association with al qaeda and iraq. and then he further, the report
9:30 am
indicated that there was some 300 names of iraqi refugees for further investigation. so, mr. bartlett, and then either of the other panelists, can you update this committee on the status of the we screening process and explain exactly what steps were taken in the event of a person with the refugee status is found that even a suspicion or a relationship of some relation to al qaeda? >> i can start briefly and then i will have to turn it over to my colleagues, but i can assure you that there's very close corporation with all law enforcement agencies, in particular the fbi. and other data we hold in our system is shared with them. on these types of cases. and certainly our cooperation with the department of homeland security to further these kinds of information sharing. but i would really need to defer to dhs to answer that with more specificity.
9:31 am
>> yes, in that regard i think i mentioned a look at about the retroactive checks that we have underway drawing upon a host of intelligence and other in the agency gave intelligence that we have available on individuals who have been, who entered the country before the enhanced checks were in place. certainly if any derogatory information comes to light as result of those rejects, that information is immediately shared with law enforcement agencies for consideration and action is approved. i do know that there've been several cases that fbi has opened as result of new information as it comes to life. for individuals already settled in united states. that said though i would have to defer really did doj for any specific form of number of cases that are still open for the status of those cases. spank you said there were 58,000 people who had been, who had come in the country during the period. do we know where they are in the united states? >> i will start with that. we know where they arrived, and
9:32 am
so certainly when people enter the u.s., we have a ranged with, in fact we contract with local agencies around the country to receive the refugees and provide initial support. largely refugee state in those initial places, but, of course, one of the great things about coming to the united states is the freedom to move. and some refugees to move so i'm not sure again if what dhs has entrance of onward movement but it is one of the issues in terms of trying to provide ongoing support to people is that you actually end up moving. but in small numbers. >> i am sort of curious about what we know about those 58,000 who are already here, and to the extent which we're going back, and do we engage them or do we go back historically and just look at other information that we have from other databases about what we knew about them prior to their time coming here.
9:33 am
because i'm struck by the fact that there was other intelligence sources, and maybe that's the way, that's the way we funded to individuals who have the past association who have actually been opposed to our military, who gained entrance to the country, but we got that from intelligence otherwise. what are we doing to look at the 58,000 who are here determine if there was anything in the background that would raise suspicion? >> if i may, i would like to note that of the 58,000 that you reference from the very outset, and large-scale iraqi processing in 2007 there was very vigorous vetting. they were being fully vetted through biographic and biometric checks. that fingerprint check were part of the process really from day one in 2007, as were other quite rigorous biographic and biometric checks. so, although some of those individuals, a subset of the
9:34 am
58,000, was that subject to the very latest enhancement. that's what ms. scalici is talking about in terms of lynette that portion of them with a retroactive check but i do want to be clear that the serious record robust setting was in place from the very beginning in 2007. but that being said, inevitably they are going to be instances where information comes to light after a refugee has been admitted to the united states. and we work very closely, whether it's intelligence community, whether it's law enforcement, or whether it's our colleagues in immigration enforcement, civil immigration enforcement, depending on the information and the circumstan circumstance, whether it's an investigation, whether it's criminal proceedings as in the kentucky cases, or another alternative in some instances is that an individual can be placed in a removal proceeding and removed from the united states. so the solutions will be different. i think from a different fact pattern.
9:35 am
the other thing that i would mention is that refugees are obliged to come forward after one year and apply to adjust their status and apply for the green card, become a lawful permanent resident. later in immigration lifecycle they may apply for naturalization. and so at this juncture is when an individual goes back to uscis, those of the application benefits can also, will also trigger additional vetting of the applicant. so there is some continuous vetting build in -- built in. >> absolutely. >> this is an interesting issue, tracking these refugees when they come here. what do we have, i mean, you said they are obligated to comment in a year, to show up somewhere and reapply. do we know if that happens? what about the ones that don't?
9:36 am
do we coming in, tried to reach out to them? and if information does come to light after they are already here, let's say, maybe even a couple years, what is our mechanism to know where these refugees actually have located? and as you said, some do move. how are we sort of keeping track of these many thousands of refugees that are here to ask if they don't automatically come back and reapply for their green card. what do we have in place? for instance, what if information has come to light on a particular person? how do we know where that person has located in this country? >> my understanding is that there is not systematic tracking
9:37 am
of refugees who come into the united states because they have concert vigorous vetting before they arrived at we do not treat them as a subset class. however, there are, the re- settlement agencies that larry mentioned, when refugees come into the united states, there is an agency that is invited to welcome them and often keep in touch with them and encourages them at the one year mark to go ahead and apply for adjustment of status. but we do not routinely track people. of course, if someone comes to our attention through law enforcement or intelligence reasons after some has been admitted, very often that information itself may include information pertaining to location. >> thank you. i appreciate that. i can see though that, and you're right, we should be treating these people as
9:38 am
suspects or criminals, but i think the issue is the information that comes to light after the rigorous vetting, at that point. there's a little bit of a vulnerability i think in this program. and i don't know if there's any talks going forward of better ways to keep track of our refugees. >> do we have a record of individuals who have been denied access? i mean, who have sought status and then by virtue of something in the past denied? >> we do maintain records on denied a refugee applicants, and those records are included in dhs is biometric database, the ident system. so if that individual is encountered again, whether
9:39 am
they're using the same identity or different identity, because biometrics to be a link -- >> is that more than a finger print? >> fingerprint and photograph. so they would be identified, and to the other, subsequent encounter would be identified that they had previously been denied as a refugee applicants. >> okay. mr. bartlett, can you explain the criteria for determining who gets this security advisory opinion? what individuals, as you were doing the prescreening, seem to bring a higher level of scrutiny. can you explain what a security advisory opinion is, and then, or if it's not, whichever panelists, but -- >> allow me one conversation. >> sure, absolutely. [inaudible conversations]
9:40 am
>> sorry, we did talk earlier about which information is classified and which is suitable for an open hearing. for the security advisory opinion check -- >> mr. bartlett, please, feel comfortable. if you're uncomfortable with talking to any kind of an issue, you have been conversant with us and i'm not against the possibility of entertaining that kind of a question in a different environment, but i just believe that we come at the same time, want to create a level of comfort that we are doing things on both ends. if you feel comfortable i would like to discuss it. >> i appreciate that. i will start with a small discussion and then i will move to the comfort level of going perhaps to offering to breathe in a classified setting. but at the outset, every refugee is subject to the consulate -- the classic check. and there is information that might be in that class check
9:41 am
could point to the need to do a security advisory opinion. and so that they can has holdings in various intelligence agencies, and that would indicate the need to do a more rigorous examination of the background through the security advisory opinion check. security advisory opinion checks are also run on other applicants, and that's what we would need to talk about i think in a classified setting, but it is one that are is one of many refugees but not all, and it does give us additional information about if there are derogatory information that would disallow their entry into the u.s. >> what do we know about applicant when they make -- this is one of the things that i struggled with, is understanding where, you know, the predicate knowledge about someone may come from. now i distinguish again when i go back to those who have worked with the government, some particular capacity over a period of time, and there's already a relationship, and i know the dod will come in and talk about individuals. they will a firm that they had
9:42 am
participated with this person. but i look towards others who come quite a privately seeking refugee status, but, you know, how do we determine that they actually have the police our relationship with some particular group, or others, that qualifies them on the first place, what predicate level of information is pursued about someone? and we have adequate resources to do it, the extent to which is probably necessary? >> sure, let me start. and then defer to my dh call it. the process by which -- dhs colleague. the process, i think i said earlier methodical and sometimes long. and sometimes, and we don't really apologize i think for the link of the process because it does allow us to be i think more thorough. again, we work very closely with
9:43 am
partners on the ground, the u.n. is one but certainly sometimes with local embassies, u.s. embassies. sometimes with ngos. to identify the refugees who are really in need of resettlement. and then we have nine contractors overseas that are located in regions throughout the world who are responsible and our our contractors, responsible for collecting additional information on each refugee family. so be it an individual or be it a family, information is collected, and that's when really we began i think a lot of the screening processes for that information. >> how proactive is that, mr. bartlett? when i was appointed united states attorney, the fbi sent people -- they talk to a degree classmates and they talk to people i went to high school with, neighbors have lived on my block when i was 10. now, of course, that's for a secure position of responsibility here in the united states to cover. i don't expect to the same degree. i'm just sort of curious, so
9:44 am
there's sort of a vetting so to speak and they would be the kind of inquiry that would go back to try to understand who this person was in their previous community and what we know about them? >> if i could, if i could say one additional point and then i think i will defer to my dhs colleague. i mean, the beginning of this process is a collection of information on each refugee or their refugee family in trying to develop both the individual information about the family but also we look at family tree information, who are they related to, collection obviously fingerprints some point down the road. so at the individual level it's collected and then that's when a process starts. at the next point of the process, department of homeland secure to comes in and conducts additional interviews face-to-face with the u.s. officer, usually located in ms. strack's office. but i would -- then unfold.
9:45 am
>> ms. strack, which also, as you discuss the process, to the extent you can share and identify how it is that that energy is designed to elicit the kind of information that would allow us to ask the next logical question about somebody's background? >> yes, sir. the information that we have on refugee applicants does a very in certain regards. .. >> has a shared a story of
9:46 am
persecution, a story of flight. they've been in the camp, they've had a ration for 20 years, they've talked about who their children are, who their family members are. so there's quite a long record on who that person is before resettlement to the united states has ever even been talked about. and so when we do the interview with that kind of a family, we will have that record in front of us, and we can elicit testimony and see if the things they are telling us are consistent with the records and the story that they have been telling to the u.n. refugee agency over a period of time, and that can give us greater confidence that the information that we're eliciting is true and accurate. in other cases we may encounter, say an iraqi applicant who has fled much more recently, iraqis tend to have of a very great deal of documentation. so when we see an iraqi refugee, we often have a passport, we have a national id, we may have a military booklet in addition to a possibly a record with
9:47 am
unhcr. they may tell us they worked for an american company, and if that's the case or with the embassy, we have the ability to go back and confirm their employment history. so it really runs the gamut in terms of the tool -- >> may i interrupt to ask whether, in fact, in light of the engagement we have with both the governments of iraq and afghanistan, do we have any access to the legacy records that the iraqi government or the afghan government possess with respect to the iraqis or afghans in their country, do we have access to those databases? >> we do have access to some former iraqi government information. i can't speak to afghanistan. as mr. bartlett mentioned, we've just seen many fewer of those cases, and i'm not familiar with that off the top of my head. but we can in some instances access that information. and then we spend really a very
9:48 am
great deal of time with our staff training them to be, um, to be rigorous in terms of e eliciting testimony. another point that i would like to mention for those who were, who claim, who have previously been affiliated with the united states, um, we have found instances where that claim is true, today did have a previous affiliation with the u.s. government or the u.s. military. we vet those individuals nonetheless just the way we would vet another applicant because we have found in some instances that individuals may have been fired for cause, or there may have been subsequent derogatory information that their former employer had no idea about. so even in a case where someone has documented prior employment directly or indirectly with the u.s. government or u.s.--affiliated entity, we still go through the full suite of security checks because we think that's important.
9:49 am
>> as we move forward and in anticipation of the -- maybe i shouldn't say anticipation, the recognition of the continuing unrest in the countries like syria and jordan, if we anticipate that there may be more demands for the opportunity to be considered as refugees for either purpose to come into our country, are we in possession of the capability right now in light of the fact that we've got resources that are screening those in iraq, we've got resources looking at afghanistan, do you have the resources on the ground to be able to sufficiently identify and do the kinds of background work that need to be done anticipating that you may get people from a broad variety of countries now who are seeking asylum under -- not asylum, but
9:50 am
refugee status in this, you know, in light of the destabilization? >> perhaps i could start just on the pure processing front. and i think my colleagues at dhs can talk more about the security screening effort. but certainly in the middle east we have very strong partners, and we have a major partner that's located in jordan. we have a major partner that's located in istanbul, turkey. and so from those two, i think, main points, um, and with some offices both in baghdad and egypt and lebanon, we do actually have the capability to receive refugees and to take initial screening information, um, and to move them through the processing system. i think on the security side i would defer to my dhs colleagues to talk about kind of our ability to vet and be ready for that potential. >> as you know, every year the
9:51 am
refugee program, the size of the refugee program is determined through a presidential determination after consultations with congress. so we know for this year the ceiling is 70,000. um, there'll be an interagency conversation and then a conversation with the congress about the size for next year. so we do feel as uscis that we have the resources we need to support a program of 70,000 admissions this year, and next year's ceiling will be set, i think, keeping the resources of all of the program partners into account. um, i can't speak directly to the capacity of the vetting agencies. um, that really is for them to say. but i can tell you that we know that a number of our vetting partners have increased their staffing, um, over the last year, year and a half or two, um, and in connection with, um, this workload and being sure that they're staffed to, um, to be partners with us in this
9:52 am
effort. >> i could, i could add, if you will, that to complement a little bit of what ms. strack said. this is a resource-spenceive effort -- intensive effort that we have in place to do the enhanced security checks on all of the refugee applicants. we have worked across the agency to include with the intelligence community. we believe they have the resources in mace right now to support the refugee program as currently configured and the current size that it currently exists. but i would have to defer to them if the program welcome back were to grow -- if the program were to grow much larger other time. that said, we continue to learn and collaborate well with our agency partners. we are working hard to try and find ways in which we can automate the processes and to streamline those processes so that over time the amount of manpower specifically devoted to the effort could perhaps go down with any loss in the efficacy of
9:53 am
the program itself. >> well, let me -- and i think it's important to note for the record because we've been asking some probing questions and asking you to more or less, you know, present your confidence that something in the future might not happen by virtue of allowing the refugees here. but i think it's important to identify the three million or so, mr. bartlett, that you said have been resettled since the, since the late '70s. is that accurate? and, of course, the 58,000 since the iraqi bulge, so to speak. so the fact that we've identified a small number who have actually come to the united states and been investigated and concluded to have participated in a potential terrorist activity is note wore ty that
9:54 am
it's quite -- noteworthy that it's quite small. but my closing question for you is we on this committee have never ceased to be i shouldn't say appreciative, i shouldn't say awed, but i would say cognizant of the extent to which al-qaeda and others constantly probe and look for opportunities to exploit our system and to introduce acts of terror not just against our tests in other parts of the country, but principally within the united states of america. to what extent can we feel comfort that al-qaeda is not looking at this program as a back door way to work with somebody to get them in here into our country to plant them for ultimate, you know, this a
9:55 am
way around the traditional way of getting into the united states of america as one would with a visa or otherwise? >> i would note as, and agree with you, sir, that certainly al-qaeda and its affiliates have been very innovative over the years in terms of trying to identify potential what they consider to be vulnerabilities or gaps in our screening procedures, try to get individuals into the united states to do harm here. that's why we definitely have an intelligence-driven process. we review intelligence on a daily 24 by 7 basis in conjunction with interagency partners to actively try to identify means by which al-qaeda or its affiliates may try to penetrate our defenses and to identify individuals or groups of concern that really require increased screening and attention. so that is, that is ongoing. certainly, we have comfort in terms of the increased security
9:56 am
vetting that we have in place through the refugee program, but i, but i will emphasize it's not a static program. we'll continue to learn lessons, we'll continue to try to identify new sources of data and intelligence that would be relevant to these screening processes and to better secure our defenses and our programs such as the refugee program. >> do either of the other two panelists have any closing comments or observations you'd like to share with us before we conclude the hearing? >> mr. chairman, i would just like to say very briefly we, when we launched large-scale processing of the iraqi program in 2007, we recognized the compelling humanitarian need, um, but at the same time we recognized in anticipation that, um, bad actors will try to take advantage of any immigration program to the united states whether it's visa programs or refugee programs or student
9:57 am
visitor programs. and so we have really vividden over the years to be in the forefront of cooperation and collaboration with the law enforcement and national intelligence communities. we know no program is impervious, but we have tried our best to be forward leaning and in the forefront and ready to innovate and learn from our experience in order to adopt the very best protocols that we can. >> thank you. mr. bartlett, any closing comment? >> just a brief one, mr. chair. i just would like to thank you for your interest in the security screening processes that we have put in place and for the recognition that, in fact, improvements have been made. and also just like to say that the security screening process not only protects the united states, but also protects the program and really allows this country to provide ongoing protection to refugees who are in need of this. so we thank you for your interest. >> well, let me conclude the
9:58 am
hearing with the same observation i made at the outset which is to thank you for the work that you do on a very, very challenging issue in which we balance the interests we have in continuing to be a nation of refuge for those who we can, um, include while at the same time appreciating the need to fulfill our first responsibility which is to protect the citizens of the united states against future harm. so you're on the tip of the spear, and i thank you for the diligent work that you're doing and the improvements that continue to be putting into enhancing our ability to do so. so i just want to conclude the hearing by asking the panelists if there should be further questioning from your panel here today or others who were unable to participate, that they may have written questions, we'll
9:59 am
keep the record open for ten days in the event that there may be further questions, and i ask that you be spnsive. and -- responsive. and i'm very grateful, again, for your participation today. so without objection, the committee stands adjourned. >> our live coverage across the c-span networks shapes up like this. at noon eastern, a discussion on the use of eminent domain as a means to restructure underwater mortgages. this comes to us from the center for american progress and features congressman brad miller who sits on the financial services committee. at 2 p.m., we'll have a look at changing marijuana laws. the focus will be on the recent legalization in colorado and washington and how the federal government will respond. that's from the brookings institution, and it's live here on c-span2 as well. over on c-span at noon, we're live from the urban institute with a program on the fiscal
10:00 am
cliff and policy implications. speakers include a former director of the congressional budget office. and later live on c-span coverage of new jersey governor chris christie and his state of the state address. tsa at 2 p.m. eastern. that's at 2 p.m. eastern. >> according to a new report, health spending in the u.s. remained low last year tracking closely with the overall rate of economic growth in the country. it says increases in medicare spending was offset by slower growth in medicaid, a trend aided by the improving economy. the affordable care act, or obamacare, had very little impact on health spending in 2011 with the exception of certain provisions like allowing those under the age of 26 to remain on their parents' insurance plans. this ises just under an hour. this is just under an hour. >> as we host the office of the actuary at the centers for medicare and medicaid services as they present their lookback
10:01 am
at national health spending this year for 2011. as you know since you have copies of the article in front of you, the central finding is that overall growth remains low, but we are beginning to see among some payers and services some signs of acceleration. and you'll be hearing more about that in a moment. in our ongoing effort at health affairs to make everybody aware of who is behind the numbers in the news, i commend to you our people and places article in this month's issue. the embargo, of course, comes off today at 4 p.m. crunching the really big numbers at cms which lays out the work of the office of the actuary and tells you a little bit more about how they do the job that they do. so as i say, i do commend that to you. i now have the pleasure of introducing the two authors who will be speaking about the
10:02 am
findings today as well as some of their associates who are on hand as well to answer any questions that may arise. first we're delighted to have with us micah hartman who's a statistician in the national health statistics group with the office of the actuary at cms. he works there primarily on historical and age-based national health spending estimates and has a bs in economics from townes zenned university. we're also delighted to have with us anne martin who's an economists in the national health statistics group with the office of the actuary. she works primarily on historical and state-based national health spending estimates as well and earned her ba in economics from the university of maryland at baltimore county. also at our table but, as i say, on hand mainly to answer any questions that arise are aaron catlin who's deputy director in the national health statistics group. he also directs the historical and age-based estimates from the national health expenditure
10:03 am
accounts and has a master's degree in management from the university of maryland, university campus. and joseph benson, who's an economists in the national health statistics group. his focus is primarily on the historical and state-based national health spending estimates. he earned an mba from ohio state university. and so with that, i'm going to turn things over to micah. >> thanks, susan. good morning, everyone. my name is micah hartman, and i'm here today with anne martin, aaron catlin and joe benson and some members of the national health expenditures account team also in the audience to present to you our latest findings through 2011. just want to remind everyone that the information that we're presenting here today will be embargoed until 4 p.m.
10:04 am
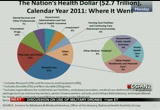
so go ahead and get into the highlights for the accounts. we see that health care spending increased 3.9% and marks the third year of stable growth at historically low rates. health care spending reached $2.7 trillion or $8,680 per person. and the health spending share of the nation's economy remained stable for the third consecutive year at 17.9%. as i just mentioned, the overall national health spending growth has been stable for the past three years. of however, at the personal health care level which includes spending for goods and services such as physician and clinic care and retail prescription drugs, there was a slight increase from 3.7% to 4.1% in 2011. the faster growth was due to an increase in the growth of nonprice factors such as the use and intensity of services. at the personal health care level, spending growth picked up for retail prescription drugs and for physician and clinical services, and from a payer
10:05 am
perspective, we see that medicare, private health insurance and out-of-pocket spending growth all increased at a faster rate in 2011. focusing on the affordable care act, we see that there was very minimal impact on the the health care spending estimates in both 2010 and 2011. this is because the most significant provisions of the affordable care act will not become effective until 2014. however, that being said, we did see only success to have and payer-specific impacts that we'd like to highlight here. for private health insurance there was an increase in enrollment due to the under-26-year-old provision. we estimate that roughly 2.7 million dependents were added to their parents' plans by 2011. the medical loss ratio, which required insurance plans to meet minimum benefit requirements, contributed to an increase in benefit spending relative to premiums for some plans. be for retail prescription drug estimates, we see that the part d coverage gap or doughnut hole
10:06 am
provision offered a 50% discount on brand name prescription drugs to medicare part d enrollees in the coverage gap which may have led to lower out-of-pocket costs for some medicare enrollees. also for medicaid prescription drug rebates or were mandated by the affordable care act which lowered the ultimate cost of these drugs. the new rebates accounted for a substantial part of the increase in total medicaid rebates in 2011. for medicare the affordable care act both lowered medicare spending through lower care updates for hospitals and certain other providers and reduced medicare advantage rates. increased also were newly-of required coverage for preventive services such as coverage for part d or the doughnut hole. on net, though, the overall impact for the affordable care act on medicare total spending was minimal in 2011.
10:07 am
taking a look at the recessionary impact on national health spending from 2008 to 2010, we see that the recession that began in december 2007 and ended in june of 2009 had a substantial impact on health care spending growth. this can easily be seen by the rapid slowdown in overall spending from 6.2% in 2007 down to 3.9% in 2009. some sector-specific areas that were impacted by the recession were first enrollment in our coverage estimates where we see enrollment in private health insurance declined by 11.2 million from 2007 to 2010. the number of the uninsured increased by seven million over the same period, and medicaid enrollment increased. other areas where slowdown impacts could be seen were private health insurance premiums, investment in structures and equipment, other private revenues and out-of-pocket costs especially in services with high out of pocket costs such as dental and
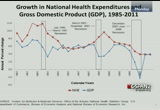
10:08 am
durable medical equipment. on this slide we present annual growth and nominal gdp from 1985 to 2011. with the three most recent recessions represented by the black rectangular boxes on the slide. as you can see, during the first two recessionary periods health care spending begins to accelerate in into the recessionary period while you can see the economy begins to slow during the recessionary period. however, for the most recent recession we see that health care spending and economic growth slow immediately, and this is likely due to many of the reasons that i mentioned on the previous slide. finally, we can see that in 2010 and 2011 both these series begin to converge in their growth, and they stabilize at roughly 3.9% for health care spending in both years. to continue the discussion about the relationship between gdp and nhe, we present the share of gdp
10:09 am
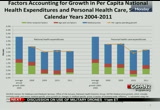
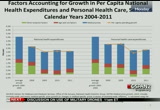
devoted to health care spending. in 1985 the share was 10.5%, and by 2011 it reached 17.9% of all health care spending. the trend on the exhibit shows the share of gdp increases just before and through a recession when the gdp begins to slow and nhe growth continues at a faster rate. this is often followed by a period of stability when the gdp and nhe increase at both similar rates. currently, we are in this period of stability where the share of gdp has remained stable at 17.9% for the past three years. on this slide we were able to isolate the factors accounting for growth at two levels of the nhe and personal health care spending. the gold line is a representation of actual per capita spending levels from 2008 to 2011. after removing population growth, the factors accounting for growth that we have isolated include age and gender impacts
10:10 am
which include both the age and gender composition of the estimates, medical prices which include both economy-wide and medical-specific price inflation and all other nonprice factors which are pictured here in green. it is a residual category and includes things such as use, intensity of services, other private revenues and all other factors including any measurement error in these estimates. the main things to focus on here are the period of growth just prior to recession from 2004 to 2008. we see that health care spending was growing at a much faster rate than during the recessionary period. we see a more immediate slowdown in 2009 for national health expenditures, and we see a more delayed or lagged impact in personal health care spending slow down not until 2010 which was mainly driven by use and intensity of services. and this was the lowest rate of growth for personal health care spending in 2010. we see in 2011 there was a rebounded in this use and intensity of services, and
10:11 am
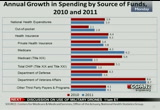
that's what we find here for the personal health care spending. if you look at it on a per capita basis from 2.9% on the gold line up to 3.3% in 2011. taking a look at the nation's health care dollar and the distribution, the $2.7 trillion was spent 31% of it on hospital care, 20% on physician and clinic services, 10% on prescription drugs, 7% on dental services and other professionals, 7% for government administration and the net cost of health insurance, and 6% for investment and nursing care facilities and continuing care retirement communities, both at 6%. all the other categories listed here round out the 100% at 14% of the total. and these shares have not changed much in recent history. taking a look at the annual growth on a year to year basis, we see that national health care spending is, remains stable at
10:12 am
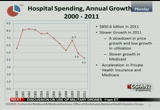
3.9% in both years, and we see this dramatic slowdown in government administration and the net cost of health insurance slowing from 8.1% down to 4.1% and a decline in public health activities from 4.9% to minnesota 0.5%. and both of these slowdowns and declines are being offset by personal health care spending from 3.7% to 4.1%, and that's mainly driven by retail prescription drug spendings accelerating as well as physician and clinical services which is accelerating too. and those two services were, goods and services were slightly offset by a slowdown in hospital care from 4.9 president -- 4.9% to 4.3%. we're going to focus on these three main categories of the nhe. hospital spending accounting for 31%, reaping $850.6 billion in 2011. it slowed down to 4.3%, and the
10:13 am
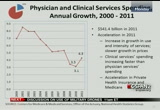
slowdown is mainly due to a slowdown in prices which we see slowed from 3.0% in 2010 to 2.1% in 2011. there was also low to declining growth in the utilization of hospital services. we saw a decline in inpatient days and a slowdown in outpatient visits in 2011. and there was also slower growth from the medicaid program which slowed from 7.6% to 2.4% in 2011. in our physician and clinical services spending estimates, we see that spending accelerated from 3.1% to 4.3% and reached $541.4 billion in 2011. we see this 3.1% was a historically low rate of growth for physician and clinic services, and the acceleration was mainly due to an increase in the use and intensity of services in physician and clinical care which more than outweighed the slowdown in prices for physician and clinical services. both physicians and clinics are contributing to the increase in
10:14 am
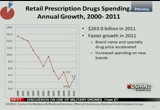
the use and intensity of services, and also what we saw was that medicare and private health insurance are both accelerating in 2011. the medicare acceleration is due to the volume and intensity of services for physician care only, and what we saw for private health insurance was an increase in enrollment after four years of decline which also contributed to this trend. for retail prescription drugs, which account for about 10% of the national health expenditures, it reached $263.0 billion in 2011, and the growth was 0.4% up to 2.9%. the 0.4% was also an historic low in 2010, and the reason for the spending increase was mainly due to faster growth in brand name and specialty drug prices as well as increased spending on new brands. we'd just like to point out that the 2.9% is still a relatively low rate of growth as you can see on the exhibit, and it's still being influenced by a slowdown in the growth of the
10:15 am
number of prescriptions dispensed, the continued increase in the generic dispensing right which is up to 70% now from 2011 up from 58% from 2007, and an increase in the number of patent expirations in 2011. so i'm going to go ahead and stop right here, and i'm going to hand the rest of the presentation over the anne. thank you all. >> thank you, micah. i'm going to touch on some of the things, um, micah's already mentioned, but in a little bit more detail. so we're going to start out by looking at the nation's health care dollar and where it came from. so i'm going to focus on the payers of health care. um, so this chart breaks down the major payers and programs and their shares of the total health care bill in 2011. um, 73% of the dollars came from health insurance which is broken out in more detail in the pie on the right.
10:16 am
um, the four largest single single payers of health care are, first, private health insurance at 33%; second is medicare at 21%; third is medicaid, a combination of federal and state and lek which which together represent 15%, and then the fourth single largest payer is out of pocket at 11%. okay. um, similar to the photograph that micah presented -- the graph that micah presented on services, this shows the annual growth and spending for 2010 and 2011. overall, you can see that the national health spending rate remained stable at 3.9%, but among the four largest payers we saw a diverging trend. we saw faster growth in out-of-pocket spending, private health insurance spending and medicare spending. and those accelerations were almost entirely offset by slower
10:17 am
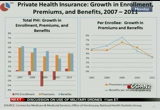
growth in medicaid. turning to private health insurance in more detail, um, we show two graphs. the one on the left has total or aggregate growth in premiums, benefits and enrollment, and the one on the right shows annual growth rates and per enrollee spending on premiums and benefits. so in 2011 both premiums and benefits accelerated, if you look at the graph on the left. they both increased at 3.8% represented by the orange and the blue bars. this slightly faster growth was the result of a gradual improvement in economic conditions and an increase in enrollment, which you can see with the red bars, for the first time since 2007. in 2011, um, there were one million more enrollees. um, in this increase comes on the heels of three prior years
10:18 am
of declines. between 2008 and 2010, 11.2 million enrollees lost health insurance coverage with 6.2 million losing insurance coverage in 2009 alone. these losses were the result of a high unemployment rate and the corresponding loss of employer-sponsored health insurance. one of the main reasons for the increased enrollment in 2011 was due to the addition of of enrollees under the age of 26. who gained coverage under the affordable care act. so although aggregate spending grew faster or in 2011 -- faster in 2011, on a per-enrollee basis, like i said on the right, we see a general slowdown in per-enrollee spending for benefits. and one reason is because people have been enrolling in consumer-directed health plans which tend to have lower premiums in exchange for higher
10:19 am
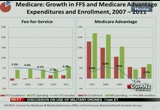
deductibles and cost sharing. also the mix of population, um, changed. those who gained coverage, namely the under-26 population, were in a segment that generally were younger and healthier. okay. for medicare we're presenting the estimates in the two distinct parts of the program, fee-for-service and medicare advantage which is managed care. um, 75% of total medicare spending is from fee of -- fee for service. and we can see that fee-for-service spending increased almost 6% in 2011 while for medicare advantage, it increased at 7%. however, when we look at it on a per-enrollee basis which is the blue lines, the recent trends are quite different. in 2011 fee-for-service per-enrollee spending increased
10:20 am
4.3%, and for medicare advantage it increased 1.5%. and there's some reasons for these differing trends. first, there's differences in enrollment growths. fee-for-service enrollment has grown only modestly in the last two years, and that follows minimal growth in 2009 and several years of declines prior to then. during the same period, medicare advantage enrollment grew at a faster rate. much of this was due to enrollees weapon ising from fee for service to managed care or just generally new enrollees coming to medicare advantage. and in addition, because medicare advantage payments are on a capitated or fixed per-person basis, physically growth and expenditures are tied to increases or decreases in enrollment. also there's factors that influence, um, payments within each of these two programs. in 2011 fee-for-service spending per enrollee accelerated
10:21 am
primarily due to, um, a one-time increase in payments for skilled nursing facilities. these were affected by a new coding structure or resource utilization group classification system. this is allowing facilities to receive higher reimbursements from medicare, but it was a one-time effect. the rate reduction, there was a rate reduction implemented in 2012 that more properly aligns payments between the new system and the previous system. second, there was faster growth in physician services, and this was due to a rebounded in the volume and intensity of services after unusually slow growth in both 2009 and 2010. okay, turning to medicaid. for medicaid, um, we show growth
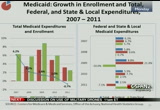
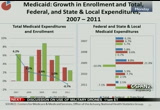
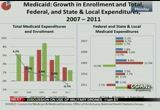
10:22 am
in total medicaid spending enrollment and spending per enrollee on the graph on the left, and on the right we break down the expenditure growth into total and federal and state and local expenditures. so in 2010 and 2011, we see slower growth in both medicaid expenditures and enrollment. in 2011 because spending increased at a slower rate than enrollment, per-enrollee medicaid spending actually declined. and the slowdown comes after recession-driven high growth in both spending and enrollment in 2009 when many people turned to the program for help after losing jobs and their employer-sponsored health insurance. and a few reasons for the slowdown include slower enrollment growth, as job growth slowly rebounded, medicaid enrollment growth began to slow. as a result, growth and spending
10:23 am
also began to slow. second, states have been under continued cost containment pressures, and in an effort to control costs, states have turned to measures such as reducing provider reimbursements, reducing benefits, restricting eligibility and increasing cost sharing. and, third, additionally these new enrollees tended to be in less costly groups such as children and families. those that would have joined during the recession that are generally healthier. on the right, um, we can see that in 2011 federal medicaid spending decreased 7.1% while state medicaid spending increased by 22.2%. and these divergent trends were due to changes to the federal medical assistance percentage formula which allocates medicaid spending between the federal government and the states.
10:24 am
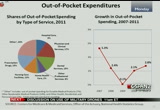
and in response to the recession, the american recovery and reinvestment act of 2009 mandated that the federal government pay a higher percentage to the states, and this, um, provision was effective from october 2008 to june 2011. in 2009 which was of of the first full year -- which was the first full year in which these enhanced matching rates were in effect, federal spending increased almost 22% while state spending declined almost 10%. and then in 2010 federal spending was still faster than state spending growth, and in 2011 when the matching rates, the enhanced matching rates expired halfway through the year, the state spending increased due to the absence of the additional federal aid. turning to out of pocket, um, out-of-pocket spending includes
10:25 am
deductibles, copayments and any amounts not covered by health insurance. and in the pie chart on the left, we show the shares of the services that account for total out-of-pocket spending. and the largest share is for individual services in 2011 were physician and clinical services, um, at 17% and prescription drugs and dental services both at 15%. and on the right we show annual growth in out-of-pocket p spending between 2007 and 2011, and in 2011 there was an acceleration, but it was still relatively slow. um, between 2002 and 2008, um, average annual growth was higher at 4.7%. so these growth rates are still relatively low. um, but the acceleration in 2011 primarily reflects the economy showing signs of recovery and also the effects of movements to
10:26 am
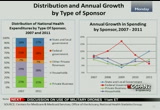
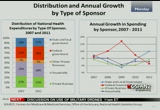
consumer-directed health plans like i mentioned in earlier in private health insurance, these plans have lower premiums but tend to have higher cost-sharing requirements. okay. now, um, we looked at national health spending, a slightly different view here, and that's by type of sponsor. these are the entities that are ultimately responsible for financing the health care bills. and they pay for insurance premiums, out-of-pocket costs or finance health care through dedicated taxes or general revenues. on the left chart, we present the shares of spending by sponsor both in 2007 and 2011. since 2007 the economic recession and legislative changes have had a notable impact on the shares of health care spending being financed by these businesses, households and governments. most notably, we see that the federal government's share increased from 23% in 2007 to
10:27 am
28% in 2011. for the other sponsors -- households, businesses and state and local governments -- their shares declined slightly during the same time period. in the graph on the right, we present the growth rates for these sponsors for 2007 through 2011. and one contributing factor to to the increased share of federal government spending is indicated by the spike in growth in 2009 with the introduction of the enhanced federal matching rates for medicaid. but another factor increasing the federal government's share was an increase in medicare spending that was financed by general revenues. in 2009 the portion of medicare spending that was financed by the federal government increased because the dedicated financing sources for medicare, which are mostly payroll taxes, declined due to effects of the recession. as the economy improves, the portion financed by general
10:28 am
revenues eases, and households and private businesses begin spending more on health care and health care coverage. additionally, when the enhanced medicaid federal matching rates expired in 2011, we see this reflected in slower federal government spending growth and increased state and local government spending as they pick up more of the health care bill. we're at the end of the presentation, and in summary these are some of the main points we wanted to get across to you today with that national health expenditures totaling $2.7 trillion or $8680 per person. this was a increase of 3.9% in 2011, and we mentioned that 3.9% was the same rate of growth as is in 2010 and in 2009.
10:29 am
national health expenditures represented 17.9% of our national gross domestic product for the third consecutive year. we saw spending grow faster for retail prescription drugs, physician and clinical services and for some payers such as medicare, private health insurance and out-of-pocket spending. however, we also showed slower, um, rate of spending for other services and payers, most notably hospital services slowed, and medicaid spending slowed. and then we showed you the sponsors of health care and how their, um, share of overall health spending has shifted between 2007 and 2011 with the highest share being the federal government at 28%. okay. so with that, um, i'll open it
10:30 am
up for questions. >> well, thank you, micah and anne. and thanks, also, to aaron and joe who, of course, were authors on the paper as well. as all of you note at the end of the paper, the $64 trillion question, i guess, ahead is whether now that we've seen three consecutive years of very slow growth in health spending, we are now on the verge of a rebounded in health care spending as we've traditionally seen after recessions. and, of course, not putting you on the spot to answer that today, but none the -- nonetheless, acknowledging that part of your work is to do the projections which we will publish later this year. obviously, this is a question you all are contemplating. as you've shown us today, we're starting to see some pick-up, the sol crime and intensity and use of physicians in particular.
10:31 am
and i'd like to start just by asking what are some of the other prominent things you're going to be watching as you put together the national health spending projections and ask yourselves whether you think we are on the verge of a major rebounded again in health spending, again, as we've traditionally seen. or whether, as some contend because of the introduction of consumer-directed health plans and other changes in the health insurance environment, maybe we won't see quite the rebounded that we've seen in the past. so, again, specifically the question is what are the key elements that you're going to be watching closely as you make these assessments? aaron? >> sure. okay. um, one thing that we note in the back of the paper is that, um, in 2011 -- as anne and micah both mentioned -- spending remained at 3.9%, so it was a
10:32 am
relatively low rate of growth. and the thing in the last paragraph of the paper, we attribute some of that to the overall modest, um, recovery in the economy and relatively slow growth, nominal gdp and in income and employment. um, so while this report does focus on the historical period, and we have seen that slowdown, our office will be releasing our updated set of projections in the summer, so, um, you can look forward to that, and that'll, hopefully, answer those questions. >> others of you want to add anything? >> i think just the focus on the enrollment and coverage estimates that we highlighted here and the state of where we were prior to the recession and where we are now coming out of the recession. so we're still not to those prerecessionary levels with the amount of coverage that's out there. as we noted, there was a large increase in the uninsured of seven million over the 2007-2010 period. so, um, so that's one, um, thing
10:33 am
that plays a direct role in health care spending, is the enrollment in health insurance coverage that we see out there. >> and, of course, looking forward we'll be looking at the effect of the expansions under the affordable care act as well. >> uh-huh. >> all right. with that, let's open it up to questions or comments or short speeches masquerading as questions from those of you in the audience. [laughter] if you would identify yourself by name and affiliation, that would be very helpful for the cms folks. so start right here -- >> bob rosen brat, freelance writer. in terms of the increase in volume and intensity of services under medicare, can you speculate as to what's going on there? why it went up compared with the previous years in the recession? >> um, well, one reason would be, um, that we talked about the expanded coverage, um, for -- i'm sorry, for preventive benefits. so that, um, did, i guess,
10:34 am
incite some medicare beneficiaries to see physicians more. but i don't know, anne, if you have more to add to that. >> where um, i don't think there's been, um, reason that we can attribute to low volume and intensity growth for 2009 and 2010. um, it just -- we're coming off of unusually slow growth in those years. so while it's still relatively slow, um, it did increase faster than 2009 and '10. and, um, i'm not sure if there's been, um, research into why the growth was so slow that year. >> okay. another question? let's move to the rear. >> bob samuelson, washington post. two-part question. um, first, in "the new york times" yesterday there was a
10:35 am
piece reporting substantial proposals by the insurance companies for premium increases that were, according to the story, double digits. it was unclear to me whether this was the individual market, the small business market or both. but regardless, it's qualitatively different from the story you're reporting here which shows increases in almost every category in the low single digits, and i'm wondering whether you can explain that. let me just leave that there for -- and i'll come back for the second question later. >> well, um, i'm -- i have not seen that report in "the new york times," but just to comment on our set of estimates, we see private health insurance is our category captures a mixture of, um, all the different types of plans that are out there including the individually-purchased and employer-sponsored health insurance. and as we mentioned, the mix of the consumer-directed health
10:36 am
plans. but our premium estimate is a mix of enrollment and the actual premium dollars being spent, you know, per plan. so those two things mixed together become our total private health insurance estimate for spending. so, um, we're probably picking up more of a real number where we have this mixed effect of people switching plans potentially when the economy gets bad and, um, maybe moving to plans that are a bit cheaper premium wise that might not cover as many things, um, different options that they look at like consumer-directed health plans and other things such as that. so -- >> is it not also the case that the lion's share of private coverage is employer-based, and the lion's share of that is large employers, and as that article in the times noted, larger employers have had a lower rate of increase in health spending in their populations recently as distinct from the smaller businesses who are still medically underwritten at least
10:37 am
until the full provisions of the affordable care act go into effect. >> yes. i mean, that's absolutely true. um, the lion's share of health insurance in this country is still provided by employers and still the majority of that's with large employers, so -- >> let me follow up with the second question. you mention on a number of cases the -- occasions the effect of consumer-driven health plans. can you define what they are and quantify that? in other words, what proportion of health plans are, quote, consumer-driven or what proportion of the population is enrolled in those plans, and how has that increased over recent years? >> um, well, we looked at a few things for this study and, um, the statistics that we quote are from the american health insurance, um, plan association, um, as well as a few other sources citing that 17% of covered workers were enrolled in a consumer-directed health plan. and that's up from 8% in 2008.
10:38 am
um, and we're reporting that on average there's about a 23% increase per year. but the numbers are not substantial. i mean, we're still at, um, you know, some estimates just show 5.3 million enrollees since 2008 have joined consumer-directed health plans. >> [inaudible] >> i think rick had -- >> if i could add something. on the first part -- [inaudible] they're talking about 2011, and can you're referring to, what, 2013 or possibly 2014 as it starts to get underway. so there's a big time difference. um, if you think also about what's happened during the recession, private health insurance where many employees either lost their jobs and host their employer-sponsored coverage or some of them, because of slow growth in wages, decided they couldn't afford their employer-sponsored insurance, and they dropped out of it. now, the ones dropping out or
10:39 am
having no insurance were typically not the ones who were the highest- cost people, those in the poorest health. those would have done everything they possibly could to stay insured, and the ones dropping out tended to have lower than average cost. now, to the extent that the employers and the insurance companies ended up with a higher-cost population and probably lost some money on that, they may not be recovering. so that might be part of what's going on. now, one other aspect, you asked about the definition of consumer-driven health care plan bs? and these have been around for a while now. they really are catching on, i fess, in a significant way. the whole idea is have insurance coverage with a high deductible and catastrophic coverage and then, typically, the employer or the plan sponsor would provide a separate fund for the individual
10:40 am
who's insured. and the idea is if a person understands they're paying out of pocket for many of their initial expenses and they have a source of information which the employer typically tries to provide as to the costs of different services and different providers and the quality of them, then they would make more educated decisions about which services to get and where to get them. um, the -- i'd have to say the evidence is mixed to date as to exactly how well these plans are working. their costs are certainly lower, but are they lower because the whole idea's working, or are they lower because healthier people tend to go for a high deductible coverage and less healthy people tend to stick with traditional coverage? that remains to be seen. >> let's take another question in the rear, please. >> thank you, jessica -- [inaudible] with modern health care.
10:41 am
could you talk a little bit about why the reasons why there was a slower or growth in hospital spending in 2011, please? >> um, sure. so the things that we mentioned, um, in the presentation and also in the article, um, the main driver being slowdown of prices. we've been at 3% growth in prices for the previous three years, and then in 2011 we saw a slowdown in prices that are being charged by hospitals. um, in addition to that, we saw a decline b in inpatient days and a slowdown in outpatient visits for 2011 reported by the american hospital association. and, um, finally, the big piece being also that medicaid spending slowed pretty dramatically in 2011, and, um, those were many of the reasons that anne already mentioned with the expiration of the enhanced federal matching percentages and the tighter fiscal conditions for states.
10:42 am
they focused on their high-cost areas, which hospitals are one of the big pieces of the budget. >> do you have any more significant information on that middle piece you just mentioned, the slower inpatient and also outpatient services? did you have anymore -- >> those are the most recently-released information from the american hospital association. >> and they have noted in the past that there has been a decline in collective services in particular over the course of the recession. >> i mean, there's still this continued shift towards outpatient services, and we still continue to see that. >> great. let me look around this side of the room and give them an equal time here. there's a question here, and then we'll come back to this side. >> [inaudible] "wall street journal." just following on the hospital trend, is there any reason to believe that this might continue in future years or that it would intersect with the trends that we've seen from physicians, retail drug usage where, perhaps, greater use of
10:43 am
physicians and drugs might, indeed, lead to more declines in hospital spending? >> yeah. again, the scope of this article is just looking at the historic period for 1960 through 2011, so that's not something we've gotten into as far as the future trends and then hospital spending in this article. um, however, our projections team will be releasing an analysis that covers that, and we also don't have the, haven't done the research as far as looking forward at, um, the trends in drugs versus hospitals. that's beyond the scope as well. >> okay. back to this side of the room. sue here in the front. >> david morgan with reuters. how does the 3.9% growth rate compare with inflation and wage growth for the period? and how do those differences, what do they say about
10:44 am
affordability? >> short answer is faster than both still, but -- >> yeah. i don't have the wage growth with me, but if you, um, you had asked about prices and wage growth, and we do have on exhibit 2 the gdp price index, so that would be the measure of price change for the economy as a whole. and whereas health spending grew 3.9% in 2011, um, the gdp price index grew 2.1%. >> [inaudible] [inaudible conversations] >> take us a second to dig it out, but -- >> i could talk a little bit, also, with our sponsor estimates. we do take a look at the household perspective, and wal have personal income. and what we've seen, basically,
10:45 am
starting in 2009 through 2011 there was a jump in 2009 from 6% to 6.3%. so a slight increase there. and we've maintained at roughly that same level of about 6.3, um, falling down to 6.2 in 2011 as a share of personal income. >> um, if i'm reading the right line, it looks like, um, cti for medical care increased 3% in 2011. so -- >> for -- >> for medical care. >> do we have all items? >> and for all items 3.2%. >> and, again, a fundamental point being because the rate of -- as we can see from the fact that the rate of g, the p, the share of g,dp related to health care has been growing roughly in line with the overall gdp. okay.
10:46 am
let's take a question right back here. >> alicia alt with img medical media. year after year it looks like a lot of the spending is just money being pushed around to different places. can you point out where there might be evidence that cost controls are making a difference? >> um, that's not something that we really focus on in this study many terms of examining -- in terms of examining cost control measures or, um, i mean, some of the things that we've seen definitely that we reported for the medicaid program was tighter fiscal conditions for states, and they looked for areas that they could, um, try to control costs and which contributed to the slowdown that we saw for the medicaid program. i don't know if others have -- >> yeah. that's the only thing we mention in the article that we're releasing today s the state efforts to control costs in the medicaid program. >> look back on this side of the room, any questions over here?
10:47 am
okay. if not, we'll come back over here. >> hi, sarah cliff with "the washington post." i was wondering if you would talk in a little more detail about what you're seeing now, how that compares coming out of previous recessions, particularly if you've seen the kind of divergent trends that you're describing with physician payments and hospital payments and whether about this time is or isn't different from previous recessions. >> well, um, some of the major differences that we point out are that the recession add a much more immediate and senate -- had a much more immediate and significant impact on health care spending than any previous recession that we've measured back to 1960. and, i mean, that's true for almost any area of the economy. and, um, we talked about the coverage impacts, we talked about, um, the loss of private medical insurance enrollment and the increase in the uninsured and the increase of individuals on the medicaid program. so, um, those were very
10:48 am
significant factors. other areas that we saw was this more immediate impact in investment in structures and equipment, and, um, also more immediate impacts on, um, out-of-pocket spending as consumers potentially, you know, lost jobs and were dealing with lower income situations. so, um, those were the differences that we saw, you know, coming out of this recession. and then we -- at the personal health care level, we saw in this lagged impact where -- we saw this lagged impact where the most dramatic or historic slowdown didn't occur until 2010. so finally hitting there, we're starting to come off of that period or off of that historic low, and now we're seeing at 2011 where we're seeing the slight increase from those historically low levels. >> come back over here for a question. >> hi -- [inaudible] washington post reporter. i realize you're going to be
10:49 am
projecting this later, but can you talk a little bit more about some of the impacts of the affordable care act and how they will play into some of the factors that have affected these numbers, how that will change things? i guess in particular the increased enrollment. >> well, the increased enrollment that we saw was from the under-26 provision, so these are generally younger, healthier enrollees. and what we did see in our private health insurance estimates is a slowdown in enrollee spending for 2011. so that definitely contributed to that trend. in terms of going forward, i'm not sure, you know, how many more under-26-year-olds there would be to add on to the policies. it seems like we've estimated it to be about 2.7 enrollees from 2010 and 2011. i wouldn't expect there to be much change with that going forward. >> to clarify, i mean enrollment of other groups moving forward
10:50 am
after 2014. >> um, well, we don't cover any of the period after 2011 for this report, so, um, it's something -- >> right. i guess what i mean is can you just sort of discuss how that would likely start to play into, i mean, given that, given that enrollment was part of the issue in terms of the slow growth rate, and we're going to be coming on to 2014, and we're going to see some major changes. can you without -- i realize you can't give numbers with projections, but can you talk about how that sort of effects all these different levers in terms of overall changes? >> yeah. >> rick. let's get a mic over to rick. >> yes. in other venues, this, of course, is the historical expenditure growth for 2011. in other venues we've talked a lot about expectations for 2014 and later. and so i'll just say a couple words about the future, but keep in mind, all of you, that this is about the past.
10:51 am
[laughter] in 2014, of course, we'll have a modest -- [inaudible] of the medicaid program, so many more people will have health insurance coverage who, to date, have not had it. likewise, with the federal subsidies for premiums and cost sharing, there should be many more people with coverage through private health insurance. it's widely known that the more coverage you have, other thicks being equal, the more services you use. they're more affordable to you, and there's that connection that a's well documented. for that reason by itself, when you get as many as 30 million more people with coverage, you would expect them to use many more services. and you would expect a higher cost. now, keep in mind at this same time that for medicaid the payment rates for providers are quite low. so on the one hand, we have much more use. but on the other hand, if somebody is currently going to the emergency room for treatment and they're having to pay for that out of project, that's a --
10:52 am
out of pocket, a very high cost if they're covered by medicaid and if medicaid has set payment rates for the providers, that would be much lower than just a normal walk-in price. i think it's fair to say that there's an awful lot of uncertainty about all of this. um, because of we don't even know, for example, which states will necessarily expand medicaid. micah mentioned earlier the elective hospitals' services that have been foregone, we believe. to what extent will those come back when people have coverage? will there be pent-up demand? also as incomes accelerate, hopefully in the not distant future, there will be greater demand for health care as we've traditionally seen. all those reasons would suggest faster growth in the future. on the other hand, and then i'll say one more point and stop about the future, um, there's a
10:53 am
growing amount of evidence that health care providers are getting it, getting that the future can't b be the same way as the past. that the future will have to involve greater efforts for efficiency than traditionally have been done. i personally don't think we've seen much in the way of results of that yet. there's some notable good examples out there, some stellar providers, but there are many more who are starting to understand that and starting to do something about it. so that would tend to help offset to the extent it's effective this pent-up demand and the increase in income and those effects. so the projections team is going to have their work cut out for them this time. >> rick, is it not also fair to say that we know overall that the uninsured use about two-thirds as much in the way of services as the insured, which would tell you, in effect by definition, as people move from being uninsured to insured, they're going to spend more, they're going to come up more to appropriate, a level that would
10:54 am
be appropriate for an insured population. so we know this, this is what we agreed to do in the affordable care act, so it will, it will unfold as we would expect in that regard. okay. let's take one more question, and then we'll wrap up. i thought i saw one more hand up -- oh, over here on this side. >> hi, matt berry with bloomberg government. more specifically on the private health insurance figure in terms of the impact of the aca and the under-26, can you define or get at more specifically the impact in terms of either enb rollment increase -- enrollment increase or spending changes due to that, the 26 and under enrollment that happened under the aca as far as the impact on the private health insurance figures you're showing? >> sure. so we quoted the figure 2.7 million enrollees added, and, um, you know, our estimates indicate approximately, you know, $1.6 billion was added to
10:55 am
private health insurance in 2011 due to the under-26 provision. um, but there's some offsets to that, too, which we mention in the paper also, the med cad loss ratio which -- medical loss ratio which lowered the net cost a few percentage points for the individually-purchased plans. and that offset was roughly around a billion dollars in 2011. >> thanks. >> sure. >> just a few moments ago rick foster used the phrase the future can't be the same as the past. and i note that the folks at the office of the actuary feel that acutely because rick, having served in the position as chief actuary since 1995, is going to be retiring at the end of this month. and this is a really momentous event not just for all of you, but for us at health affairs and many of you who have been dealing with the office of the actuary and particularly with rick for quite some time. rick, we did not want to let you
10:56 am
go without having a book of memorabilia, and so we prepared a book of every single health spending projection as well as historical health spending that has been published since health affairs came into existence in the early 1990s. [laughter] and, of course, since most of this is available for free on our web site, this gift is worth absolutely nothing, and, therefore, will not violate any federal restrictions against a gift that you might receive. [laughter] but i did just want to read you briefly from the note that we have at the beginning of this volume. dear rick: on behalf of our entire team at health affairs, and my predecessor, thank you for your service to our nation as chief actuary of cms and warm congratulations on your well-deserved forthcoming retirement. your 40-year career in the federal government has left an indelible mark. your contributions to health
10:57 am
affairs are unmatched as evident in this impressive compilation of analyses by the office of the actuary that we have published over the past 30 years. we're grateful for your leadership and objectivity in producing this important work. we will miss both your professional expertise and your friendship. we convey our best wishes for your happinesses, fulfillment and, of course, for your good health in your next chapter. warm regards from the team at health affairs. so, rick, please come up -- [applause] >> thank you very much. >> thank you very much. i don't know if you want to say a few words? >> hardly ever avoid the opportunity. [laughter] >> okay. >> i'd just like to thank you, super, for those very nice, very thoughtful, very kind, overly generous remarks which i quite appreciate. it has been a long career looking back, you know, there
10:58 am
are enough of us in the audience -- i won't mention robert pare or ricardo, anybody else who's not as young as they used to be. but the older you get, the faster time goes by. and you look back, and can you think of all the different things that have happened, and they seem like yesterday. in reality they're 10, 20, 30 years ago. i leave the office of the actuary with a lot of pride in what the office has accomplished. not only the nhe area which susan has very nicely summarized for me, but in assistance to congress, evaluating the financial status of the trustees' report, assisting anybody who's needed help including a lot of you in the press. and it's not that easy to be objective, it's not that easy to be independent, it's not that easy to be nonpartisan particularly as the world around you grows more and more partisan
10:59 am
as you all recognize. so the office has accomplished this, and i know it will continue. i'd like to think that the office will do even better and greater things after i leave. if they're only a little bit greater and a little bit better immediately, that's okay with me. [laughter] thank you all very much. thank you, susan. [applause] >> thank you all, and we will look forward or to seeing you later this year as we bring out the projections and, of course, in between as we bring out other issues of the journal -- >> live coverage across the c-span network shapes up like this: live here at noon eastern, a discussion on the use of eminent domain as a means to restructure underwater mortgages. this comes to us from the center for american progress and features congressman brad miller who sits on the financial services committee. at 2 p.m. we'll have a look at changing marijuana laws. the focus will be on the recent legalization in colorado and washington and how the federal government will respond.
11:00 am
that's from the brookings institution, and it's live here on c-span2 as well. .. i enjoy the capitol hill coverage because i started there many decades ago with your coverage live of the house and senate, and, also, certain committee hearings, they are informative to the public to see what happens in congress. like the fact c-span presents itself of what's happening, a little bit of comem tear, but not edited out to a certain prelix, but what they want to present to the people. c-span j created by
11:01 am
america's cable companies in 1979 brought to you as a public service by your television provider. >> a discussion now on drones and cyberattacks as tools as modern warfare at the recent halifax security forum, participants talked about the resource to find attacks and rules for engagement with unmanned drones. speakers include elisa massimino of the groups human rights first. this is about an hour. >> thank you very much. nice to see all of you. thank you for sticking around for our last session. you will remember in the debates that president obama made quite a sensation when he said we have fewer horses and bayonettes because the nature of the military changed. that launched thousands upon
11:02 am
thousands of tweets and means and how appropriate was that given the fact that one of the new instruments of war is the mouse, the joy stick. we're going to discuss those evolutions of technology today and what they mean and whether we've adapted to them adequately in terms of our strategies, in terms of our legal system, and in terms of our capabilities. we have a great panel to talk with us today. i'll introduce them one by one. at the end, there's mohammed abulahoum, head of yemen's justice party. there's vic toews, and elisa massimino, president and ceo of human rights first. we have general gene jean-paul, and we have rafal rohozinkski,
11:03 am
ceo of the general, starting with you, since this is about the evolution of warfare and you're the man of nato and in charge of making it all happen. talk to us if you would, frame the issue in terms of what you see as the challenges, what nato has to do to adapt to the new world. >> first and foremost, we heard during those few days that the future is very unpredictable to let's try just to enable it as key enabler for doing that. our onlied forces today are facing tremendous challenge. the world is changing. the environment is ever adapting, the threat is multifaceted. the risks are there. so what is the answer? the answer is with nato, israeli working on more giant,
11:04 am
responsive, connected forces, well-trained, and at joint and combined level and forces, how we do that in a harsh constraint, fiscal constraint in in our point of view, focus on three trends will are related to the panel here. first and foremost, a more effective command and control chain. coming from the political level down to the politician level giving the power to the executive level to do the mission. this is mission command. secondly, a reliable, relevant intelligence. would be able to feed the chain of command in the most fast way as possible. thirdly, foster a adaptive,
11:05 am
safer engagement of forces in order to optimize, maximize the use of force while minimizing the end desire effects. there are in, in point of view, two key factors in that, two key enablers. first and foremost, man and women. key factors. there are those dedicated people that must be trained. they must be skilled enough. we must educate them, and they must get the tools that we can our to them. the most suitable tools. i will suggest this system on our part, obviously, provided that we can control it as we can control the ethics that we will discuss of later.
11:06 am
this men and women really are multipliers now, but they rely on information, everything rely on information. the management of information is the second key enabler. we can collect everywhere in the world gigabytes of information, and we can process that in the most secure way. we have to manage that. we have to use that. we have to improve that. we have to share that. as we come into the information sphere, we must take into account not only data and the system, but as well the users, the providers, and the users of those skills, and this is the link between the two key enablers. those users are the skilled
11:07 am
people who are able to use information to understand information, to put this back into context, and then to transform it, the information, into intelligence. to transform information into action if required. if only we master information, we can properly form decision making process. we can accelerate the tempo of the operation, and we can create dramatically our effectiveness, and we can answer strikes. this is what i call cyber. this is, from my perspective, an interconnected information process with many players. we have to play together. this is not only the issue for military, but military as a key role to play because of the mission, because of the skill so how we train together, we work
11:08 am
together, how we provide information to the guys who need it, this is the actual challenge for the military forces of the 21st century. >> you general, a quick follow-. how far along are you in the transformation, and how long will it take? >> transformation is not new. nato has taken the case for -- i mean, command -- the command information, ten years, and nowadays, you have 28 countries working together down in norfolk. we are working on many initiatives to answer to the demising of the force. connecting the forces together, force initiative, to make sure we train, that we get the best technology in the proper way in the short delay to make sure that the people on the ground the airmen, the sailor, have the
11:09 am
proper weapons to do the job, and it could be connected for everybody with information. >> i want to have a little fun here and lay out a scenario and see how the panelists would deal with this. let's say there's coordinated cyber attacks on canada's power grid. generators destroyed. the grid comes down. people do not have gas. people cannot use their atm machines. the power loss has spread to the united states because of the way the grid is constructed. transportation comes largely to a halt, financial institutions are unable to do what they do. yoif -- you've got a big problem on your hand. minister, toews, who has to worry about this? >> going along with the
11:10 am
hypothetical situation, this is certainly something we focused efforts on in terms of addressing. we have the military, of course, who deals with the incoming issue, how to stop it, prevent it, and mitigate the damage that's being done, and we have my department, the department of public safety, that deals with the coordination of not only provincial governments and the federal government, but also with the private sector, and especially larger power corporations, gas pipelines or hydroelectric power. we signed agreements with the americans to make sure that that information flows across the line to the americans so there is a high degree of coordination, not only on a national basis at every level of government, but also with our close international allies. >> how confident are you that you could, at this moment in
11:11 am
time, detect such attack, stop such attack, or that you have things in place to mitigate the attack or recover from them? >> we're -- we believe that we are as good as anyone else in the field. >> well, that's not encouraging to some people. [laughter] >> well, i think -- i think you're not giving enough credit to our allies, and our allies are very much on top of this situation. we've heard what the general said in the military context. i'm also very encouraged by what our allies are doing in a civil context, so i think that we can respond very quickly in order to deal with the situation. will we will able to address the entire issue immediately? it really depends on the nature of the concern that we're meeting. the evolution of the concerns happen so quickly, and i think
11:12 am
the -- the bombing of the twin towers is an example of how we never thought of that scenario in many respects issue and i think the same thing is true in the cyber context. >> most of the power grid, all of it in some instances, are in the hands of private company. >> right. >> does that pose a particularly challenging thing for you? can a government impose or require or ask of those companies certain protections, and will they put them in place if they are not required? >> i think that we've had a very good dialogue with the private corporations, and, also crown corporations in this country, many of them control the power grids and that. we've had good agreements. we announced that agreement with the private industry and power companies in canada about two years ago now when we invested $90 million in the development
11:13 am
of our own coordination within the federal government, but, also then working with the private sector and power corporations. >> but do we have to worry about the grid? >> we always have to worry about the grid. it's foolish to think that we have solved the problem, that we can go on to new challenges. this is a problem, i believe, certainly, speaking at this point in time, that will never be fully resolved. >> i know you want to chip in here, but there's a specific question first. can forensics tell us where these attacks came from? >> to answer the question directly, the question of attribution, seen as the speed bump preventing us from prosecuting these investigations, but it's a legal and political problem more than one of practicality. i want to go back to the question you asked the minister, one that raises two issues. do we currently have situational awareness in national cyberspace the way we do in other environments, air, land, sea,
11:14 am
space? >> what's the answer? >> the answer's no. the answer's no because of the vast majority of what we describe with cyberspace, the infrastructure, the technology, the products, the application layer that constitute this social, technical environment is in the hands of the private sector, and there's privacy laws, corporate responsibilities that prevent the government from having complete transparency over that environment. at the same time, cyberspace, as it exists now, largely built upon the ip protocol was built for resilience, not security. it's uniquely vulnerable to penetrations and mall feasance, but it's also a remarkably self-healing system. i pause at the example of a massive disruption of the power grid is a slim possibility because of the nature of the network itself. it doesn't mean we shouldn't address the policy levels of the situational awareness, that's
11:15 am
critical from the due diligence point of view, ect., but it's not the only thing required to introduce security. >> do you have suggestions on how we get that capability? >> yes, i do. one of the things we overlook is when discussions happen about the ability of states to work with private sector over cyberspace and res of -- and issues of privacy, we forget the issue of cyberspace, the telecommunications carrier is the queen. this is where infrastructure, data, and network all come together. we forget telecommunications is the most regulated industry we have. our ability to incentivize telecommunications carriers to detect anomalies at scale that would essential hi address 90% of what we see as malfeasance in cyberspace is quite possible, but we have not taken that step.
11:16 am
>> rafal, pushing back on the attribution question that you don't see as that big of a challenge, i guess. if i bought a laptop with cash, and i created malware, and i stripped all the io dent fieres out of it -- identifiers out of it, traveled to a foreign city, went to an internet cafe with unsecure wifi, and launched malware, erased the disk, and i dumped that computer in the dumpster, that malware in that one computer could be enough to bring down the critical infrastructure of a city. could you track me down? could you find me? >> let me answer the question by tieing into something that the general was talking about. i think we forget that times of conflict are generally a great catalyst for technology and organizational advances. we saw the emergence of the concept of air-land battle
11:17 am
coming out of world war i, developing in world war ii, to the old era, and we tested the consequences of the space age. the main innovation coming out of the last ten years in the global war on terror is an evolution applying intelligence in warfare. currently the head of the cia, and previous director of intelligence in jsoc in afghanistan and iraq said in the cyber era, intelligence and maneuver are our fire. the act to be able to generate data from vast distributed services to aggregated and share effectively create actionable items is a huge advancement responsible for, for example, the ability to interdict ied networks in iraq before they were anal -- able to form, okay? that same kind of cross disciplinary analysis made possible by the fusion of data
11:18 am
and analytical systems is exactly what would solve the problem of attribution. it doesn't matter where you are. the ability to correlate data at scale through a variety of means makes the difference. i think attribution is doable. from a legal point of view and ethically is a different question. >> that's where i want to go next. elisa, so canada and the u.s. both affected by this hypothetical scenario, and there are rumblings about possible retaliation. rumblings of possible drone strike because, in fact, they traced this to aqap in yemen. do they have the legal basis to retaliate? >> well, i think that the, you know, one of the -- i agree very much that in times of crisis that's when there's great technological developments, and there can also be during those
11:19 am
periods of time an impulse to, you know, look for a whole new legal frame work or structure that governs that, but, in fact, i think as you said, we have a very strong legal frame work for thinking about some of these issues. it may not answer all of the questions that come out of this new technology, but i think it's a pretty solid place to start, and so, you know, one of the questions that people ask in the context of a cyberattack like the one you described, jean, is can this be an act of war that triggers the laws of war or self-defense, the laws of self-defense that entitle a retaliatory attack, and i think that's a clear one. i think it does. >> let's ask the general. do you agree with that? is that an act of war, this hypothetical scenario? >> recognized in 2010 in lisbon
11:20 am
that cyber was a real threat for collective defense, in part of collective defense. that's why they set up a number of expertise as well, and it would be to really to nato alliance council to decide if it's the case, provided we are set up now. >> have you established what the threshold is? i mean, for instance, in this case, if i talk about the power grid down, potential lives lost because hospitals ran out of fuel for the generators, but what about something more like the sere -- series of lesser attacks we see now? instead of the bombing of a factory, people get the information, and at what point are those acts of war? >> we had a discussion involving
11:21 am
most politicians and strategy commands with exactly that kind of scenario, and it came after a few days, a kind of consensus, but the analysis of the ethics, and that's what comes at the end of the day, and as well as the di simulation of the threat, we shouldn't overreact, and we must remind ourselves that security and cyber security is firstly and foremost the responsibility of each nation. we have to deal with responsible global defense, collective defense, but with every nation responsible for its own security. that's the treaty. >> elisa, back to you for more on this legal situation. you say we may have a frame work for dealing with it, but have we started dealing with it? >> well, i think, you know, attribution will be a big question in this scenario if you
11:22 am
want to then retaliate or knock out the networks that lunched the attack. you have to know where they are and how they get it. those are fairly conventional questions in war, i think. i'm assured to hear that we would be able to track you down, jean, when you go to the cyber cafe and launch your attack, but the question about overreaction that the general raises, i think, is a really, really important one, and in this situation of evolving technologies, which those of you here on friday night for dinner and heard our dinner speaker lay out a fairly horrifying scenario about how quickly we, technology is advancing, we really don't have any time to waste in terms of thinking about how we're going to deal with this frame work, and it raises some very significant questions for our democracies, for our civil liberties, for our privacy, for
11:23 am
executive power. these are questions that cut across the issue of cyber warfare that we have offensive and defensive, frankly. we learned recently the u.s. and others engaged, already, in a cyber offense with respect to iran and the development of the nuclear program. we have to, before we launch all of this, think through what rules of the road are we -- >> but we already have launched it. >> well, yes, like i said, time's a wasting. we need to be thinking about whether it's the cyber offense or the drones in particular. they have become such a favored technology in countering terrorism. one counterterrorism in the -- adviser in the u.s. said drones are a tactic, not a strategy. if you rely too much on one tactic, there's a risk it becomes your strategy, and, yet,
11:24 am
drones are, in a way, like a lawn mower. you know, you have to keep using it. you mow your grass, and when you stop, it grows again. it's not a strategy. it's a tactic. that raises significant legal and moral questions for us about the laws of war. >> mohammed, going to you. in the hypothetical scenario, it's been attributed to aqap in yemen. the u.s. decides to stage a drone strike, and they take out a couple of terrorists, but they also take out ten civilians, including women and children, so has the u.s. created more terrorists than its eliminated? >> i think one of the most important things we have to look at is technology is advancing so fast that sometimes we become so afraid not knowing what's the middle of the line. an example of what's happening, yemen and the drone, i think if you look at the drone use in
11:25 am
yemen in the last seven months is different than it was used a year and a half ago, and, let's say, before the arab spring and why i go back to the arab spring? i think dealing -- before arab spring, the use with the drone is regimes were using or working with the west or especially with the u.s. to settle scores with areas in yemen or groups in yemen, and that created a big fuss. today, that strategy is more open and more open regimes like in yemen to a great extent. i think we've seen more drone attacks than in the past, but there is a serious cooperation, there is a serious cooperation. you target the enemy, know who the enemy is, and this was on account of both sides. i think the most important thing to keep in mind is that where do you -- what do you stop the use of the drones? what are the consequences later
11:26 am
on? so far -- >> what's your thought on that? >> the consequences, for me, and i think i strongly believe that, we cannot continue just using the drones. you have to complement the drones with other strategies. when you strike in a friendly area is different when you strike an enemy area. i think yemen cooperated seriously, and i think yemen is one of the very few countries that managed to draw out from certain areas, of course, with the help of the u.s. and the west, but what worries us most is that the collateral damage can be a serious problem. use the drone, but don't overuse it. don't depend on it. if you ask me today are the drops doing a good job? i prefer to see the drones, the damage would be -- but how limit the damage? then, the other important thing is how can you help after drone
11:27 am
strikes? you have to go in with development. you have to go in and make aide. you have to go in with education so that you push out with those drones and make sure they don't come back. you don't want to strike, then leave, and do nothing. they come back in multiples and bigger and bigger, and that's the worry for us all. >> and won't go away. >> exactly. >> i don't see the moral or legal responsibility any different than a manned aircraft. there is collateral damage that is done using your expression with a manned aircraft. that does not lessen the moral and legal responsibility on the commanders to ensure that we minimize collateral damage and to ensure that we properly understand what the target is that we have properly attributed so i simply see the drone as a technological development, but it doesn't relieve us of any
11:28 am
miranda -- moral or legal responsibility. >> quickly to you. >> i agree with that, and one of the biggest purported advantages of the drone is they are accurate and reduce collateral damage, but the questions, i think, the big question, the use of drones raises, relates much more to the -- to the legal questions around who is targetable which are really, really important. you know, if you have a legal frame work or a policy frame work as the u.s. has, that sweeps into the mix, say, all military aged males in a particular area or the so-called signature strikes that the u.s. have engaged in which really relate to behavior and not identity. it's not the kill list; it's different. you have to ask questions has that frame work gone beyond the laws of war that we want the
11:29 am
world to follow roughly. >> i think we need to separate the drone discussion from just the kill and capture missions we are discussing here right now, and what it represents as a capability for modern military. the extension of the isr platforms is not unique to kill and capture. the assistance surveillance that could put troops forth with aid, whatever, on target as appropriate, i think will be greatly aided by technologies whether the canadian forces is deployed on another afghan mission or doing humanitarian relief in haiti for that matter, but this is the future of how to employee our forces. it's not longer amassing tanks, but applying intelligence and information to put precise forces on target. i think in terms of the ethical question is different. if we look at the laws of war, and we look at, first of all, necessity, should we be using it? is what we're doing an application of violence? is it justified?
11:30 am
a political decision to make, obviously. distinction, are we actually targeting the right individuals opposed to indiscriminantly targeting another population? is our response comes rat to the attack? in those cases, you know, whether or not we have a moral problem with targeted killings, it fits the criteria well rather than dropping a bomb in a place in hopes of solving a problem. >> general, you want to weigh in here? >> two comments on drones. firstly, i mean, as far as precision is concerned, it's not the drone, used as a platform by the operation. according to the rules of the engagement, they use that very wisely with realtime intelligence which is good because it treats targets, and this is the best use of drones i would suspect. if you need more fire power,
11:31 am
then you need something else. suggesting a fighter aircraft or some origin, and the second point is that the drones are usedded nowadays in, i would say, benign, ground to air threat. when you use drones over a very well prepared country, we will use those strategies, and then we can be in great trouble if we rely on drones. there is a strategy, but drones are a wonderful tool for collecting information. we know that. we try to improve that, and in nato, we have a real good plan to include it. >> mohammed, did you want to weigh? >> drones are another generation. in five or six and seven years, we will be talking about something else, but the most important lesson we have to take to mind is there has to be
11:32 am
serious cooperation, a very close cooperation between both countries that is launching the drone and the country that is hit, and the other important thing is intelligence. intelligence has to be precise and accurate. you have to go and make the precise intelligence. don't just go in and strike in an area where you create more mess than preventing. the most important thing is that take speedometer. -- take responsibility. whatever goes wrong, take responsibility, and make sure you don't make that mistake again. by doing these things, drone can be used, and like the minister, it's like any other warfare we cannot avoid. >> i want to bring the audience in this. i have a lot of people in here passionate about the issues. there's a hand up way back here in the back of the hall. if we can quickly get a microphone. there's other people. if we have another microphone, come down here, there's a gentleman with his hand up. >> thank you, it's a short
11:33 am
comment or question, madam, on where should the threshold for nato, collective defense be on a cyber attack, and i suggest that we should not have a threshold because there's very good reason to have a strategic foreign enemy so perhaps you would not know what he can get away with, thank you. >> anyone want to react to that one? internally, do you have to know what the threshold is though? >> i would say that you have to be very careful in maintaining strategic ambiguity about what you, you know, what we stand for in terms of the what we would constitute an act of war that would trigger such a response because, again, keep in mind that in this area as in many others, we set the rules of the road. by our behavior, we set out the rules, and because the
11:34 am
technology is advancing so quickly, this is technology that the bad guys are going to have very, very soon so we need to be fairly clear about what we would consider a threshold for retaliation. >> let me jump into this because i think it ties into the question we had earlier about situational awareness. on a data level, canada's largest carrier on a daily basis absorbs denial of defense attacks that a magnitude 20 times larger used in 2007. >> wow. diswh -- >> the reason they can do that is because the absorb the cost of doing it by passing on the cost to consumer. there's no threshold by the government saying this amount of bad traffic constitutes something to look at from a perspective of being part of national security. that's part of the problem that we see cyberspace as a domain in which we have freedom of navigation and always have,
11:35 am
okay? we somehow assume that, for example, it always supports our isr efforts and have the aibilityd to command and control because we own the technology. that's not true. you know, even though we have not defined it, our peer competitors have. russians talk about a national telecommunications asset. the chinese talk about it in terms of information dominance within international telecommunications space. i think until we define it in those terms, and that's a political decision, not a technical decision, we will berf whether something crosses a threshold or doesn't. >> another question right here. >> lincoln bloomfield. i want to ask a question about drones and one about cyber and get a reaction from the panel. i'm interested in the legal and policy frame work for both, each of which, i argue, has the technology and applications moved quickly, and the policy
11:36 am
has work to do, but putting our finger on what works or what to do is difficult. these questions come from experience in the military and cyberspace war gaming environment. you have not mentioned drones are called "unmanned veebs," and so the whole point is there is no pilot to kill with an antiaircraft gun. no one dies on our side. deaths happen on the battlefield. the question i have for you is if an unmanned attack were launched from a place in the united states, killing someone in the battle space in the middle east, and somehow the adversary managed to penetrate that space in the united states and bomb that facility killing people who were part of the command and control from the comfort of the united states, is there anyone in the panel arguing that was not part of the battlefield? i'll leave you with that question. is there anything -- would you say that's an attack on the homeland, if they bombed us in america, or say, well, it was the battle space because the
11:37 am
trigger was pulled from that facility that killed that adversary so if they managed to vike you back, it's no different from shooting a pilot downright above the battle. >> hold the second question. get an answer to that one. general, do you want to tackle that? >> i refuse -- if i may, the term "unmanned," drones land a lot of good kills, and takes intelligent people to use it at its best, and as you say, somewhere in the loop, there is map, there is skill, there is commander. many more people is the case to operate a single system so this is a first point, and the second point i made. we must be very careful about the actual threat against the drone. we are misleading, if we think this is the only and single way
11:38 am
to be used today. it's a very benign environment over libya. it was in afghanistan, yemen, those threats, what will be the case when we start losing these drones which cost more and more. this is our supplier, when in war terms, only the u.s. gets a number of drones that are shootable. to push that, that kill people, and proper command. >> he didn't directly answer the question, but he did in a way in describing the frame work and all of what's behind the so-called unmanned armed vehicle is the command and control structure and military light and
11:39 am
that's military target in a conflict as you described so i think i don't -- i didn't hear any argument that that was somehow an illegitimate military target. >> [inaudible] our homeland by using -- including the command and control chain from the homeland. may i ask the cyber question? >> first, mohammedmented to -- mohammed wanted to weigh in. >> quickly. this is where we have to think we draw the line. we don't want to go into a conflict and you think you are going to close a front, and then you end up opening several fronts of the it's very important that you have to be focus. you have to know what you are targeting. you have to have a strategy and a plan. you cannot just wake up in the morning and say, yeah, today i'm going to strike in yes , yemenr tomorrow. you have to coordinate with others and look at the drones as a way as just like a manned plane or gun or anything that you have to use it and use it well, and the consequences --
11:40 am
the results are not right, the consequences will be damaging to both sides it's very important to look at that. >> second question. >> quickly. if the u.s. used offensive cyber to try to stop an add adversarym slowing the force so you hit systems trained to hit power grids, whatever it is, hinder the ability to muster. if, by hitting the networks with a cyber attack that bled into the sighfullian -- civilian society and caused the gdp harmed, hospitals civil harm, anyone argue as a legal matter, the president of the united states would be responsible for the the quote-own-quote of collateral damage on third and fourth order of cyber attacks? >> one thing to say i think stock games proved that you can treat sib space like any other
11:41 am
weapons platform means there's propagator code that delivers code finely targeted to hit certain targets. it's nonsense to talk cyber security without thinking about it in offense and defense. when we send men and women own peace keeping missions, they are trained. we have to think in terms of cyber in exactly the same kind of way. because cyber weapons are largely defined in termings of legal liability, what you talk about, who they effect and what they effect, and because code gives us the ability to make that quite precise, again, olympic games proved that, it's a reality that we have to get over. >> general, nato and offensive capability? >> nato, the main -- the coalitions of nato is about collective defense, and secondly, cooperation security.
11:42 am
>> no offensive capability? >> each country can have its own policy which is different. >> we have a young woman back here. go ahead. >> from washington, d.c.. i want to ask the question about the drone program. drones, when used connectively, they are shrouded in secrecy. it's held tightly, but the effects of such acts are decidedly not, and we see the populations reacting very strongly to these. knowing the precision of the drones, what's the obligation of the nations using drones in a kinetic matter to be open, conduct diplomacy around them, and are we doing a good job on that now? >> elisa? >> on the last part of the question, speaking from someone watching the united states and we're doing a better job than we
11:43 am
were before in terms of transparency and talking about what the legal frame work governing the decision making. that's a huge series a couple weeks ago in "the washington post" about the deposition matrix and more transparency around the decision making for drone strikes, but there is a huge disconnect between an understanding of what is -- how those decisions are made and the reporting about the effects of the decisions from the u.s. government in terms of who is killed in the assertion there are virtually no civilians killed in the strikes, and what's reported on the ground, people on the receiving end of the drones so we have a long ways to go, i think, and unfortunately, not to ballet a dead horse, but i think it's one of the most important reasons why we have to get more clarity about this is that everybody else in the world is watching what we do and what we say, and
11:44 am
drawing from that what the frame work is without us saying that, you know, we consider this -- a legally binding frame work, and so we are, by default, telling the russians, the chinese, and anybody else that these are the rules that govern when you get the technology. that's a serious, serious problem. i talked to senior military commanders who express great concern. they say, you know, this technology's great, and it enables us to keep people further out of harm's way delivering what we need to deliver to the enemy, but i sure hope that others are not going to copy us and -- >> but they are. they will. >> that's the question. >> rafal, you wanted to weigh in. >> i just wanted to restate what i said earlier. if you look at laws of armed conflict, necessity, distinction, proportionality. distinction and proportionality, we don't have a problem with, but necessity is a political issue. we have to be better at
11:45 am
describing what the war aims are in order to be able to then justify the distinction and proportionality. that's the problem. >> on distinction, i think this goes to the point if there's not transparency about how we're distinguishing between who is, you know, targetable with lethal force, then we can't really articulate we comply with a principle of distinction than important. >> general mcchrystal was quoted as saying i want to go to bed with more friends and fewer enemies. the fewer enemies relates to the fact they were able to disable the ieds in iraq by targeting very, very effectively. he was not saying who they were targeting, but that's part of the secret. we have to recognize that secrecy as part of military operations is a necessity. political explanation over the goals of military action, that requires transparency.
11:46 am
>> of course we need secrecy about the identities, nobody questions that, but we're in a situation right now where you cannot get a clear and consistent answer across the government between the pentagon and cia, for example, that operating different drone programs under seemingly different rules about what is the decision making framework about who falls into that category of lethal targettability and who falls outside of it, and that's one of the biggest problems. >> we have another question here. minister, weigh in. >> in this context, the principles are no different than in respect to the use of any lethal force. i don't understand how drones are somehow different from new technology. the political, the legal, the moral responsibility remains exactly the same. the issue of clarity. the communications with the public, these are exactly the same. i don't see drones creating an
11:47 am
additional legal or moral responsibility that should not already be address the -- addressed in our traditional mechanisms whether it's law enforcement or military actions. >> go ahead. >> we use drones in the very vague war on terror, but we see also the use of drones in very different areas, you know, to survey trarvegging -- trafficking and other parts so it's getting into the civil criminal law. one of the major problems i see, and i would like to know your take on it, is that the use of drones is actually ruling our legal frame work because drones, at the same time, secret service collecting information, the intelligence service, they are law enforcement, they track down people, and then they are executers, executing the death penalty so i mean, without or beyond every legal frame work there is, so there are dangers
11:48 am
ahead. >> general? >> only include the death penalty if you decide to. it's about the rules of engagement, the chain of command and control, and who controls the weapons, and i do agree. it's saying that any of the weapons other than it's more visible that some other covered operations, but at the end of the day, the question is still the same. how the commander -- when the commander decide that should really strike that, this is the issue. on the other hand, this is a real true value in using drones in many areas. i do agree. they are very multiple capabilities, and in the u.s., they use that for crisis, stops, for many, many mission.
11:49 am
>> over here we had a question. >> i'm from lebanon. how possible is international cooperation when it comes to technological and cyber warfare and technology? especially between technologically advanced countries and developing countries? i'm linking that to a recent development in the region with nonstate actor, hezbollah, sending drone over israel. yes, there can be expected or usually expected reaction which is a military retaliation by israel to destroy the drone and potentially later destroying military installations inside lebanon, but if we want to keep the situation safer for us as lebanese people, is there a point of thinking about international cooperation and through technology to diffuse and reduce the technological capacities of nonstate actors to create situations that can lead
11:50 am
to terrible problems for the whole population? >> there's a big one. who wants to handle it? >> well, i think the questioner pointed out a very important point. i think it gets back to attribution. who are we dealing with? who is the threat? is it a criminal threat? is it an act of war? we have to be very certain before we begin to react to a certain situation because that will determine what the target will be. i think the general has outlined the -- some of the very important principles, the collection of information, the analysis of that information, and then the action. the cooperation, for example, that goes on between the five eyes community is quite intensive in canada, great
11:51 am
britain, united states, australia, new zealand, we share information very, very clearly to ensure we are fully informed before we make decisions, and that's wonderful. we do extend that to other countries, of course, through nato and otherwise, and, of course, people realize the extent of that cooperation, but i think we also have to look at where the -- where the threat is emanating from. the situation in lebanon where lebanon may not actually control aspects. i mean, how fair would it be then to retaliate against a city in lebanon or a community in lebanon when it may be a criminal act, but in another situation where the central government has a more fulsome control, there is a responsibility, i think, of countries to approach that country and say there is a
11:52 am
threat emanating from within your borders. you have a responsibility to determine that, and i think as we become more interconnected, as we become more interdependent in terms of our cyber economy, all of these things, all of these countries, whether you're a debtor nation or creditor nation, all have an interest in ensuring that the cyber system works, and so i think that we need to continually reach out to countries, and i think hold individual countries responsible. clearly, the lebanon situation or the yemen situation is a different situation, and afghanistan is different where the central government does not have full control, but i would suggest that in areas where the central government is fully in control, there is a internal responsibility for that country to act because that is simply a
11:53 am
criminal action that needs to be addressed by the domestic government. >> you wanted to way in, mohammed? >> i think an important point focusing on technology, but there is a human factor. if you look at the human factor, and if you look at the middle east as talking about the lebanon groups and what have you, and the last two or three years, are we better off or worse off? i think we are better off, not due to the drone or the technology, but rather there is more openness. there is more cooperation. we mentioned, yesterday, i think that there is a big opening for closer cooperation on a long term, and, today, the radical groups are not just a threat to the west, but they are a threat to the muslim countries, arab countries, more than a threat to the west. how do we work on pushing and not just focus on drone technology, but rather push ideology out this is something to focus, and technology is something that's like a switch. it's like an electric switch, on
11:54 am
and off, but will not do the main job we hope we can reach. we have to keep that in mind. >> staying with lebanon and another example that's not the drones, that's the cyber attacks so one of you mentioned cyber attacks, american cyber attacks on iran, and so say hypothetically or factually that iran is revenging through a number of very senator young men and women who are congregated in the southern district of lebanon, which is completely under the hezbollah control, and so what are the rules of engagement then? what would happen? there is an attack, by the united states or israel, a cyber attack that's targeted iran, and iran is avenging through discreet networks in lebanon, which, authority the government cannot control the area. what happens then? should we expect?
11:55 am
is there anything to do about it, or do we live with it? >> yeah, i think your question goes to a much broader issue, and that is on the interstate level, we don't really have an agreement of what an ease clay story model looks like. that becomes more complex when we are thinking about the fact that in many cases the capability to create weaponnized code resides in the codes of non-state actors because all the sudden we lack, in effect, the extension of what we conventionally looked at, rules of war, international mechanisms of dealing with risk to the application and use of force. i think this is a big problem. look at how cyber has been employed defensively, it's not title 10, which means it is not under the use of the armed forces, but the intelligence function. i think that's the case for most countries that the general eluded who develop capabilities other than defense, that they
11:56 am
declare on the nato level. it's a big challenge, you know, and one that i think right now, we are starting to face by and large because it's being forced to us in the sense of having to engage with the issue of governance of cyber states at large. next month, there's going to be a meeting in dubai at which many of the countries falling under the up -- umbrella of the itu vote to take away the governance, the administrative standards of the internet away from icam, a u.s. based entity, and to the united nations. the principle reason why this is being pushed by china, by india, by russia is because they want to see a reterritorialization along those lines. it's a prereck cigs for them to create a model that's attributable, and, secondly, because for them, cyberspace is
11:57 am
not a threat to them in the way we see it, threats to network, but what's done through those networks. population, given the ability to express views unpopular to regimes, popular mobilization in the way we've seen it in the arab spring. i mean, i think the fact that we sometimes talk different languages at the international level, we lack mechanisms is a huge gray area that sometimes is in or advantage, herego, the case to use drones in yemen, and sometimes a huge disadvantage, and i look to the minister to deal with cyber criminality where the jurisdictional problem effectively mean we cannot address the main root cause of some of needs issues. >> we a question back here, and when you are done with the question, pass the microphone forward to david. >> thank you very much. tom malinowski. the title of the session refers to automatic weapons, and at the risk of taking us a couple
11:58 am
decades in the future, i wanted to ask about the next generation of drones or robotic weapons which are under development today, and which will be designed to have a man out of the loop, to be able to select their target and deploy their weapon without human intervention. the military advantage is obvious. they will make decisions to receive information and make decisions vastly more quickly and efficiently than a human soldier, and that seems to me that if our adversaries develop weapons, the pressure on us to keep up in that race would be enormous, but the question is should we go there? should we even begin that process? can we trust a machine weapon in effect to make those decisions about distinction and proportionality on the battlefield to determine the value of the human life as
11:59 am
compared to civilian life? what kind of world would we live in if a dictator like a future assad had an army of robotic weapon that fall any order because unlike human beings, robots always follow orders. should we go there or think today about drawing a line, of fully autonimous weapons. >> in a way, it's technofedism. they are possible because of the way of the infrastructure that's behind them. that are the pointy edge of the speer, but the decision, the ability to go from a hyper deductive form of gathering to an inductive form of analytics, using patterns, i worry about
88 Views
IN COLLECTIONS
CSPAN2 Television Archive
Television Archive  Television Archive News Search Service
Television Archive News Search Service 
Uploaded by TV Archive on

 Live Music Archive
Live Music Archive Librivox Free Audio
Librivox Free Audio Metropolitan Museum
Metropolitan Museum Cleveland Museum of Art
Cleveland Museum of Art Internet Arcade
Internet Arcade Console Living Room
Console Living Room Books to Borrow
Books to Borrow Open Library
Open Library TV News
TV News Understanding 9/11
Understanding 9/11